
Quantum encryption helps fix big cybersecurity problems. Many experts say quantum computers can break current encryption. About 62 percent worry about keeping data safe. Big tech companies spend billions on quantum information. Quantum cryptography is like a dimmer switch, not just a light switch. It makes things more private and keeps communication secret.
Key Takeaways
-
Quantum encryption keeps data safe from future attacks. It uses the laws of physics, so it is stronger than old math-based ways.
-
Quantum key distribution lets people share secret keys in a safe way. It can tell if someone tries to spy, so it keeps messages private.
-
Using quantum-safe tools now helps groups stay safe. It also helps them get ready for the future as quantum computers get stronger.
Quantum Threats
Breaking Classical Encryption
Quantum computers bring new dangers for data safety. Regular encryption, like RSA and ECC, uses math that is hard for normal computers. Quantum computers use special algorithms, such as Shor’s and Grover’s, to solve these math problems much faster. This lets hackers break into systems that use old encryption.
Here is a table that lists the main quantum threats to regular encryption:
|
Quantum Threat Type |
Targeted Cryptography |
Impact Description |
|---|---|---|
|
Shor's Algorithm |
Asymmetric encryption (RSA, DH, ECC) |
Breaks public key cryptography by factoring large numbers and solving discrete logarithms. |
|
Grover's Algorithm |
Symmetric encryption (AES) and hash functions |
Makes brute-force attacks faster, reducing the strength of algorithms like AES-128. |
|
Harvest Now, Decrypt Later |
Encrypted data storage |
Attackers collect encrypted data now and decrypt it later when quantum computers become stronger. |
|
Compromise of TLS and VPN |
Key exchange and authentication |
Threatens secure web and VPN connections, requiring new cryptographic solutions. |
Quantum cryptography and quantum encryption try to fix these problems. They use the laws of physics, not just math, to keep information safe. Hackers can already save secret messages and wait until quantum computers can break them. This is called a “harvest now, decrypt later” attack. Important data, like government secrets or personal info, could be in danger even years after it was sent.
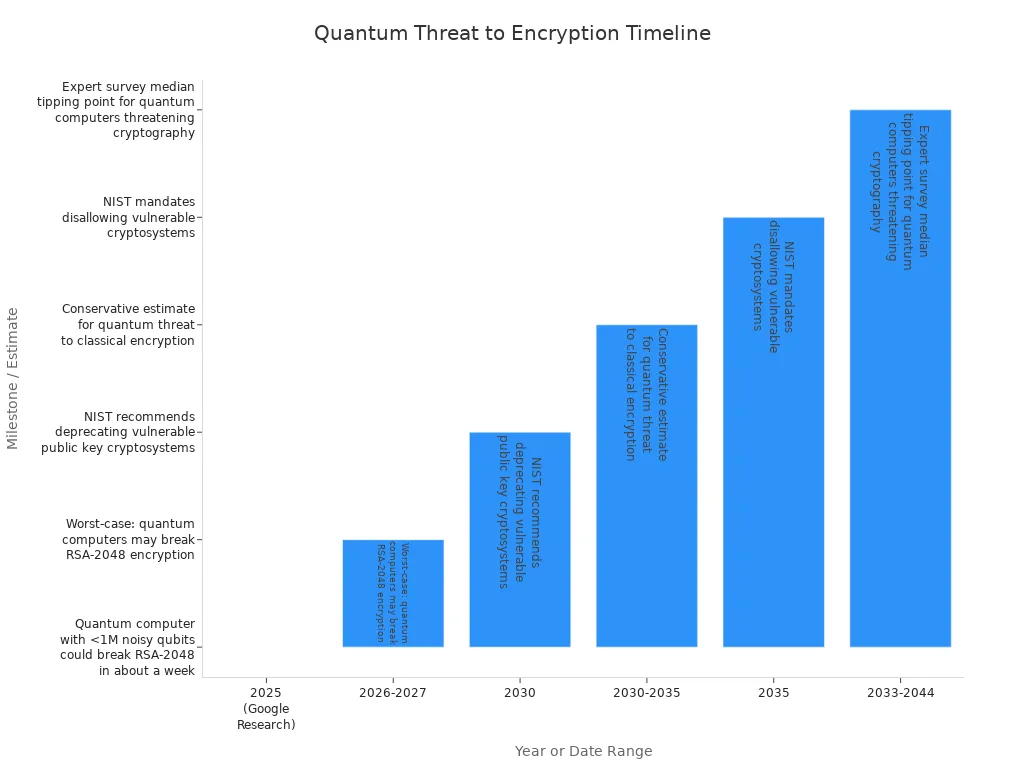
Post-Quantum Cryptography
Post-quantum cryptography uses new math problems that are hard for quantum computers. These new algorithms help keep data safe in the future. The National Institute of Standards and Technology (NIST) worked with experts around the world to make new rules for post-quantum cryptography. In August 2024, NIST shared three new rules for quantum-resistant encryption and digital signatures. NIST says groups should start using these new rules now to stay safe from quantum threats.
Quantum cryptography is not the same as post-quantum cryptography. Quantum cryptography uses quantum physics to spot spies and keep messages safe. Post-quantum cryptography changes old algorithms so quantum computers cannot break them. Both ways help protect quantum information and keep data safe as technology gets better.
Quantum Encryption Solutions
Quantum Key Distribution
Quantum cryptography helps people keep their information safe. It uses quantum physics to protect secrets. Quantum key distribution, or QKD, lets two people share a secret key. No one else can know this key. They use the key to lock and unlock messages. Classical methods use hard math, but quantum cryptography uses nature’s rules. Even a super-strong computer cannot break the security after the key is shared.
The most used quantum key distribution protocols are BB84 and E91. In BB84, one person sends random bits with light particles called photons. The other person measures these photons. They compare what they did and keep only the matching bits. If someone tries to listen, the photons change. Both people can see there is a problem. E91 uses pairs of photons that are linked, called entangled. If someone spies, the link breaks. The two people see mistakes.
Quantum key distribution keeps secrets safe for a long time. It protects against future attacks, even from quantum computers. This is different from classical key exchange, which can be broken if computers get stronger.
Here is a table that shows the main differences between classical and quantum cryptography:
|
Aspect |
Classical Cryptography |
Quantum Cryptography |
|---|---|---|
|
Security Basis |
Hard math problems |
Quantum mechanics |
|
Vulnerability to Quantum Attacks |
Yes |
No |
|
Long-term Security |
Limited |
Proven by physics |
|
Eavesdropping Detection |
No |
Yes |
Quantum encryption uses these ideas to keep quantum information safe. It helps protect data and keeps secrets private for many years.
Eavesdropping Detection
Quantum cryptography does more than just share keys. It also helps people know if someone is listening. This works because of special rules in quantum physics. When someone measures a quantum system, it changes. If a spy tries to read the message, the message changes. The sender and receiver can see something is wrong.
Quantum encryption is like a seal on a package. If someone opens the package, the seal breaks. Everyone knows it was opened. In quantum cryptography, if someone tries to catch the photons, the photons change. The sender and receiver check some of their data. If there are too many mistakes, they know someone tried to spy. They throw away the key.
Some important rules make this work:
-
The Heisenberg Uncertainty Principle: Measuring a quantum state changes it.
-
The No-Cloning Theorem: No one can make a perfect copy of a quantum state.
-
Superposition: Quantum bits can be in many states at once, but measuring them picks just one.
-
Entanglement: Linked particles show changes if one is measured.
These rules help quantum cryptography keep secrets safe. People can trust their quantum information stays private. If someone tries to break in, the system shows clear signs. The users can stop talking.
Quantum encryption and quantum cryptography give new ways to keep secrets safe. They protect against strong computers and help people know if their messages are private. This makes them important for the future of cybersecurity.
Adoption and Challenges
Implementation Barriers
Many groups have trouble using quantum cryptography. There are several big problems:
-
Sending quantum keys far away is hard. The signal gets weak and noisy. This makes it tough to keep messages safe.
-
Special tools are needed, like single-photon sources and detectors. These tools cost a lot and are tricky to use.
-
Most systems need direct optical links. They do not work well in big networks.
-
The devices are often big and need careful setup. This makes them hard for people to use.
-
Some systems can be attacked in other ways. These attacks do not break the math but use side channels. This makes people worry about safety.
-
Different systems may not work together. There are no shared rules or standards.
-
Quantum repeaters help send signals farther. But these are still being made and tested.
-
Money and rules also slow down how fast people use quantum cryptography.
Tests show that secure keys can be made over 100 km. But the signal gets worse as the distance grows. New ideas, like using machine learning, help control noise. This makes the system work better. Companies and scientists want to make the tools smaller, cheaper, and easier to use.
Future of Quantum Cryptography
Big tech companies are adding quantum-safe tools to their products. Here are some examples:
|
Company Name |
Country |
Quantum Encryption Integration |
|---|---|---|
|
SandboxAQ (Alphabet) |
USA |
Post-quantum cryptography solutions and hybrid AI-quantum sensor technologies. |
|
QuintessenceLabs |
Australia |
Quantum Key Distribution (QKD) and Quantum Random Number Generators (QRNG). |
|
Post-Quantum |
UK |
Post-quantum cryptography and quantum-safe VPNs. |
|
ID Quantique |
Switzerland |
QKD for secure key exchange in sensitive sectors. |
|
Infineon Technologies |
Germany |
Hardware-based quantum-resistant encryption solutions. |
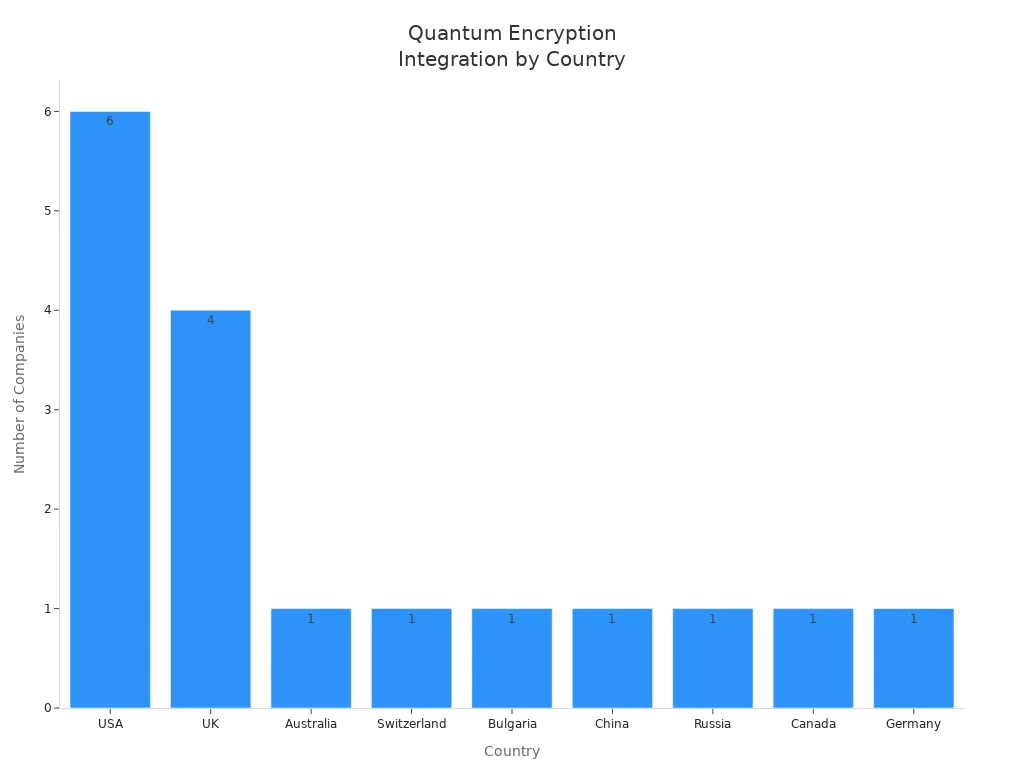
Governments help groups get ready for quantum security. They say to check which systems use public-key cryptography. They also say to update rules and plan for a safe change. The U.S. and NATO want everyone to use post-quantum cryptography by 2030-2035. Some banks, governments, and even fancy phones already use these new tools. These phones have special chips to keep data safe.
Groups that get ready now will keep their data safe. They will also be leaders in the new quantum-secure world.
Quantum solutions help fix big cybersecurity problems. They stop future attacks and keep key exchanges safe. They also help find out if someone is listening in. These new tools make data protection stronger. Experts say groups should check for risks. They should watch for new rules and update their systems. Learning about changes helps everyone get ready for safer communication.
FAQ
What makes quantum encryption different from regular encryption?
Quantum encryption protects data using physics rules. Regular encryption uses hard math to keep things safe. Quantum encryption can tell if someone is spying.
Quantum encryption is safer because it shows if someone listens in.
What problems does quantum key distribution solve?
Quantum key distribution helps people share secret keys safely. It lets two people make a secret key together. No one else can see or copy this key.
What devices use quantum encryption today?
|
Device Type |
Example Use |
|---|---|
|
Secure calls and messages |
|
|
Bank networks |
Protecting transactions |
|
Government systems |
Safe communication |
These devices use quantum encryption to keep things private.







