
If you want the best privacy, you need the best encrypted communication phone. Here are the top 10 choices for 2025:
-
VERTU Agent Q
-
Blackphone PRIVY 2.0
-
Purism Librem 5
-
Sirin Labs Finney U1
-
Liberty Phone
-
VERTU METAVERTU MAX
-
Bittium Tough Mobile 2C
-
Apple iPhone 17 Pro Max
-
Google Pixel 10 (with enhanced security)
-
K-iPhone
You want a phone that keeps your encrypted messages safe. You also want your privacy protected. These phones are special because they provide strong encrypted messaging. Their hardware blocks threats, and their software is designed for privacy. More people want encrypted phones every year. Look at these numbers:
|
Metric |
Value |
|---|---|
|
Market Size in 2024 |
$3.39 billion |
|
Projected Market Size in 2025 |
$4.07 billion |
|
Expected Market Size by 2033 |
$17.41 billion |
|
CAGR from 2024 to 2033 |
19.93% |
|
Growth in demand for encryption-secured apps |
74% |
|
Growth in BYOD implementations |
79% |
|
Increase in mobile workforce security needs |
61% |
|
Surge in end-to-end encryption deployment |
65% |
|
Rise in encrypted communications |
74% |
|
Increase in mobile identity verification |
60% |
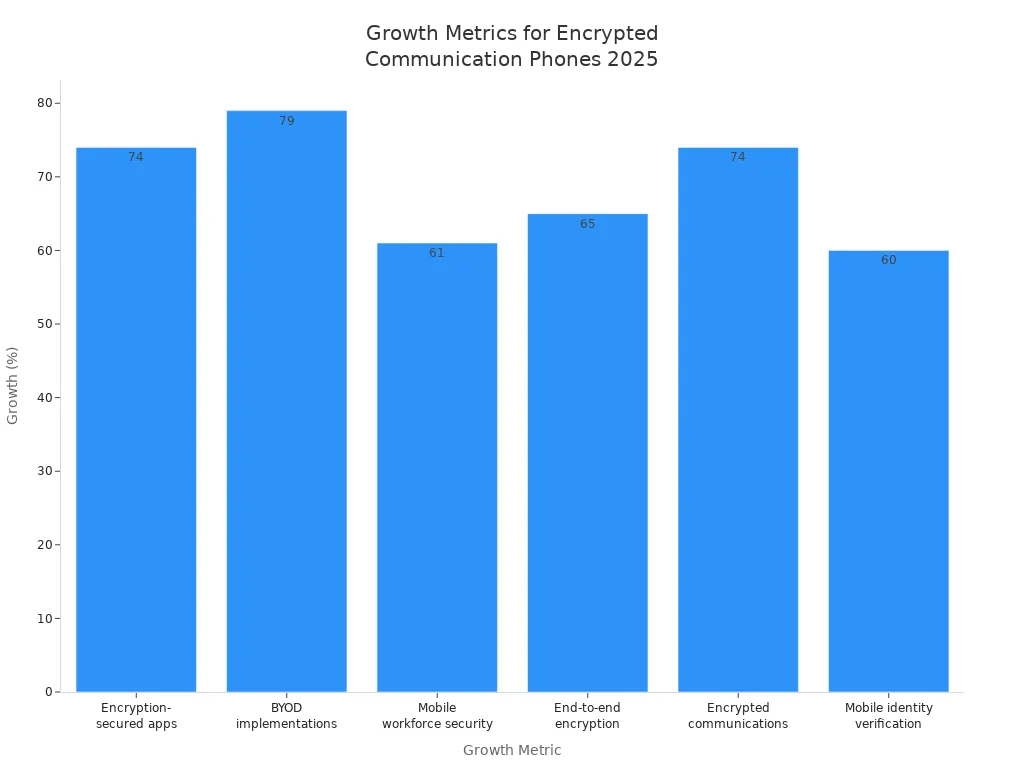
You can see why encrypted phones are important. Privacy and security matter more every day. As you read, think about what privacy means to you. Consider what the best phone for privacy looks like for you.
Key Takeaways
-
Encrypted phones help keep your privacy safe. They stop hackers from reading your messages. Look for things like end-to-end encryption and secure operating systems. Hardware kill switches also make your phone safer. Think about what you want to keep private before you pick a phone. The market for encrypted phones is getting bigger fast. This means more people want better privacy. Every encrypted phone has special features. Pick one that fits your life and security needs.
Privacy and Security Criteria

How We Selected the Best Encrypted Phones
You want a phone that keeps your information safe. We picked these phones by looking at what helps protect privacy. First, we checked if each phone uses strong encryption like AES, RSA, and ECC. These help keep your data safe from hackers. We also made sure each phone has an operating system focused on security and privacy. This means you get updates often and less chance of getting malware.
We looked at hardware security, too. Some phones have kill switches for the mic or camera. You can turn them off easily. This helps you feel safer. We checked privacy policies as well. It is important to know how your data is used. Phones with strong privacy settings and clear rules scored better.
Here are the main things experts look for:
|
Criteria Type |
Description |
|---|---|
|
Mobile Device Security |
Stops people from getting in and blocks bad apps. |
|
Device Encryption |
Uses cryptography to keep your data safe. |
|
Application-level Encryption |
Adds extra protection for app data. |
|
Trusted Key Storage |
Keeps your encryption keys protected. |
|
Protected Communications |
Secures your calls and messages on networks. |
|
Remote Wipe |
Lets you erase data if your phone is lost. |
|
App Whitelisting/Blacklisting |
Controls which apps you can use. |
|
Compliance Checks |
Makes sure your phone follows security rules. |
|
Root and Jailbreak Detection |
Checks if your phone’s security is still strong. |
|
Auditing and Logging |
Tracks security events for you to see. |
Key Security Features to Consider
When you pick a secure phone, you want features that protect you every day. End-to-end encryption is very important. It keeps your calls, texts, and files private. Only you and the person you trust can read them. Secure operating systems give you better privacy and regular updates. You also want strong encryption for stored data and data sent over networks. This keeps your information safe even if someone steals your phone.
Look for hardware kill switches. These let you turn off the mic or camera yourself. No app or hacker can use them without your permission. Secure messaging and privacy-focused apps help keep your chats private. Secure communication apps use strong encryption to protect sensitive data.
Here is a table that shows how encrypted phones are different from regular ones:
|
Feature |
Encrypted Phones |
Conventional Phones |
|---|---|---|
|
Encryption of Data at Rest and in Transit |
Uses strong encryption for all data. |
May have weak or no encryption. |
|
Secure Operating System |
Focused on security and privacy, with updates. |
Easier for hackers to attack. |
|
Protection against Malware and Threats |
Controlled apps and better protection. |
Can get malware from unsafe sources. |
|
Privacy of Calls and Messages |
End-to-end encryption for secure chats. |
Weak or no encryption, may leak information. |
|
Features and Applications |
Secure app stores, remote wipe, self-destructing messages. |
Less control, easier for cyberattacks. |
You want a phone that puts your privacy first. Pick encrypted phones with strong encryption and good privacy settings. These features help you keep your digital life private and safe every day.
Best Encrypted Communication Phones 2025

VERTU Agent Q
Do you want a phone that is private and fancy? The VERTU Agent Q is special. It has a handmade look and smart technology. The phone is split into three parts: Main, Secret, and Ghost. Each part keeps your stuff safe with encryption. Your calls and messages are always protected. If you lose your phone, you can erase everything with a remote command. This makes sure nobody can get your data. You get up to 10TB of storage that cannot be changed or broken into.
|
Feature |
Description |
|---|---|
|
Multi-layered architecture |
Splits the phone into three safe parts with encryption. |
|
End-to-end encryption |
Keeps your chats and calls private. |
|
Remote ‘kill' command |
Lets you erase your phone so nobody can get your info. |
|
Distributed vault |
Gives you lots of safe space for your files. |
An AI helper helps you plan and do tasks. Edge Autonomy keeps your private stuff on your phone. If you want a secure and fancy phone, Agent Q is a good pick.
Tip: This phone is great if you want privacy and style.
Blackphone PRIVY 2.0
The Blackphone PRIVY 2.0 is good for work or government jobs. It uses end-to-end encryption for calls and video chats with the Silent Phone app. ZRTP keeps your calls secret. You can send safe messages and share files too.
-
Good for people who work with secret info.
-
Used by government workers who need safe phones.
-
Great for anyone who wants strong privacy.
You can trust this phone to keep your secrets safe. It is one of the best encrypted phones for privacy.
Purism Librem 5
Privacy fans like the Purism Librem 5. It uses Matrix and XMPP for safe calls and messages. The phone runs PureOS, which is open-source and secure. You can turn off the mic, camera, and Wi-Fi with switches. This stops hackers from spying on you.
-
Purism is adding encrypted calls to the Phosh interface.
-
Matrix and XMPP help keep chats and calls safe.
-
Soon, you can make encrypted calls with Posh-Calls.
|
Pros |
Cons |
|---|---|
|
Switches for extra safety |
Some software problems |
|
Easy to fix and change |
Not many apps |
|
Made with care and good materials |
Sometimes slow |
|
Focus on privacy |
Costs a lot (starts at $799) |
If you want a phone you can control, Librem 5 is a strong choice. You get privacy and can change things how you like.
Sirin Labs Finney U1
The Sirin Labs Finney U1 is good for people who use digital money. It uses blockchain to keep your transactions safe. Every transaction is clear and cannot be changed. Hackers find it hard to break in. You get safe logins and strong encryption. These features protect your digital stuff.
If you use crypto or blockchain, Finney U1 is a smart choice.
Liberty Phone
Liberty Phone is made for people who want hardware safety. It has switches for the modem, Wi-Fi, mic, and camera. The phone runs PureOS, which is open-source. The modem is kept away from the CPU. This makes it harder for hackers to get your data. Liberty Phone is made in the U.S., so you know where it comes from.
-
Switches for modem, Wi-Fi, mic, and camera
-
Runs PureOS, an open-source system
-
Modem is kept away from the CPU
-
Made in the U.S. for more trust
If you want hardware privacy, Liberty Phone is a great pick.
VERTU METAVERTU MAX
VERTU METAVERTU MAX is a fancy encrypted phone. It uses cool materials like carbon fiber, calf leather, lizard skin, and alligator skin. The phone feels nice to hold. It has two chips: one for encryption and one for speed.
|
Feature |
Description |
|---|---|
|
High-End Material Selection |
Uses special materials like leather and carbon fiber. |
|
Exceptional Craftsmanship |
Feels fancy and well-made. |
|
Dual Chips for Performance |
Has an encryption chip and a fast chip. |
-
Encryption chip keeps transactions safe.
-
Snapdragon chip makes the phone fast.
If you want a secure phone that looks amazing, METAVERTU MAX is for you.
Bittium Tough Mobile 2C
Bittium Tough Mobile 2C is for people who need top security. It is approved for government and business use. It meets rules like CONFIDENTIAL, NATO Restricted, Common Criteria, and FIPS 140-2.
|
Certification Type |
Description |
|---|---|
|
CONFIDENTIAL (NCSA-FI, TL III) |
Approved for secret chats. |
|
NATO Restricted Level |
Good for NATO secret talks. |
|
Common Criteria |
Follows ISO/IEC 15408 rules. |
|
FIPS 140-2 |
Meets U.S. rules for encryption. |
You get strong encryption, a safe system, and hardware protection. If you work for the government or need a safe phone, this is a good choice.
Apple iPhone 17 Pro Max
Apple iPhone 17 Pro Max has new privacy tools. AI runs on your phone, so your data stays private unless you use the cloud. The eSIM cannot be taken out if your phone is lost or stolen. This keeps your info safe from thieves. You also get easy setup for travel eSIMs in iOS 26.
-
AI works on your phone, keeping data private.
-
eSIM cannot be removed if lost or stolen.
-
Easy setup for travel eSIMs in iOS 26.
If you want a safe phone with familiar features, iPhone 17 Pro Max is a good pick.
Google Pixel 10 (with enhanced security)
Google Pixel 10 is a top encrypted phone for Android fans. It uses the Titan M2 chip for hardware safety. AI blocks scam calls and texts before you get them. The phone has dual eSIMs, so you do not need a SIM card. Google gives seven years of updates, which is longer than most Android phones.
|
Feature |
Google Pixel 10 |
Standard Android Security |
|---|---|---|
|
Hardware Security Chip |
Titan M2 chip |
Depends on the maker |
|
Scam Detection |
AI blocks scams |
Basic call screening |
|
eSIM Support |
Two eSIMs |
Usually one SIM |
|
Update Commitment |
Seven years of updates |
Often shorter support |
You also get Face Unlock and Fingerprint Unlock. If you want a secure Android phone, Pixel 10 is a great choice.
K-iPhone
K-iPhone is for people who want Apple’s security and extra privacy. It uses AES 256 encryption between storage and RAM. Apple’s Data Protection makes a key for each file. The Apple File System lets different parts of a file have their own keys. The Secure Enclave keeps important info safe for Touch ID, Face ID, and Apple Pay. This keeps your data away from the main processor.
-
iOS uses AES 256 to encrypt memory.
-
Apple uses Data Protection for files and keys.
-
APFS lets files have different keys.
-
Secure Enclave is a special chip in iOS devices.
If you want Apple’s best encryption and privacy, K-iPhone is a top pick.
Note: Each encrypted phone has something special. You can find the right phone for you, whether you want fancy, open-source, or government-level safety. Always think about your privacy and what matters most.
Encrypted Phones Comparison Table
You may want to know how these encrypted phones compare. It is helpful to look at their main features and prices. This table shows the top encrypted phones for 2025. You can find which phone matches what you need.
|
Phone Model |
Key Features |
Price Range |
OS/Security Focus |
Best For |
|---|---|---|---|---|
|
VERTU Agent Q |
AI agent, multi-layered encrypted storage, luxury design |
Custom/Luxury |
VAOS, Edge Autonomy |
Entrepreneurs, Leaders |
|
Blackphone PRIVY 2.0 |
End-to-end encrypted calls, secure messaging |
Silent OS, ZRTP |
Business, Government |
|
|
Purism Librem 5 |
Hardware kill switches, open-source, encrypted chat |
$799+ |
PureOS |
Privacy Enthusiasts |
|
Sirin Labs Finney U1 |
Blockchain wallet, encrypted transactions |
$999+ |
Sirin OS |
Crypto Users |
|
Liberty Phone |
Hardware switches, US-made, open-source |
$1199+ |
PureOS |
Hardware Privacy Fans |
|
VERTU METAVERTU MAX |
Dual chips, luxury materials, encrypted chip |
Custom/Luxury |
METAVERTU OS |
Luxury, Security Seekers |
|
Bittium Tough Mobile 2C |
Military-grade encrypted comms, certified secure |
$1800+ |
Secure OS |
Government, Enterprise |
|
Apple iPhone 17 Pro Max |
On-device AI, eSIM lock, encrypted storage |
$1199+ |
iOS |
Everyday Users |
|
Google Pixel 10 |
Titan M2 chip, AI scam block, encrypted updates |
$999+ |
Android, Titan M2 |
Android Fans |
|
K-iPhone |
AES 256 encryption, Secure Enclave, file-level keys |
$1299+ |
iOS (customized) |
Apple Security Seekers |
Tip: Encrypted phones often cost more than regular ones. For example, Blackphone PRIVY 2.0 starts at $825. A Google Pixel 9 Pro costs about $999. Some phones, like Sikur One, need a yearly subscription for encrypted services.
Each encrypted phone has something special. Some focus on hardware privacy. Others use AI or blockchain for extra safety. If you want the best privacy, look at the features that matter most to you. Do you want hardware switches, a fancy design, or strong encryption? The right encrypted phone will help you stay safe and keep your privacy every day.
How to Choose an Encrypted Phone
Assessing Your Privacy Needs
You need a phone that matches your life. First, think about what privacy means for you. Do you want to hide your messages at home or work? Maybe you need to keep business secrets safe. Some people want to stay hidden and use a fake name or number. Others care about how much data apps take from them.
Here are some questions to help you pick a secure phone:
-
Do you want calls and texts to be end-to-end encrypted?
-
Are you worried someone might get your phone?
-
Do you want your phone to erase messages quickly?
-
Is it important to use the same apps as your friends?
-
Do you want features that block tracking or hide your location?
You can use this table to match your privacy needs to the right phone:
|
Consideration |
What to Ask Yourself |
|---|---|
|
Privacy goals |
What do I want to keep private? |
|
Privacy guarantee |
Do I need legal proof my data is safe? |
|
Number of parties involved |
Who else will use or see my phone? |
|
Flexibility |
Will my privacy needs change soon? |
|
Performance |
Do I need a fast phone for work or games? |
|
Transparency |
Can I check how the phone protects my data? |
Tip: Think about your daily routine and what you want to keep safe. The best encrypted phone will fit your needs.
Evaluating Security Claims
Many phones say they are very secure. But how do you know if they really are? You can use tools like Mobile Verification Toolkit, Oxygen Forensic Detective, or Magnet AXIOM. These tools help you find out if a phone has hidden spyware or weak spots.
You should also read about the phone’s encryption and privacy features. Look for reviews from people who care about privacy. Some phones let you see how they work, so you know they are not hiding anything. If you want to be extra sure, ask if experts have checked the phone.
Usability vs. Security Balance
You want a phone that is simple to use and keeps your data safe. Some secure phones are harder to use. You might have trouble adding apps or using some features. Phones with the best privacy can feel less friendly.
Here is a table that shows the trade-offs:
|
Aspect |
Stock Devices (Easy to Use) |
Custom Secure Smartphones (More Privacy) |
|---|---|---|
|
Usability |
Very easy |
Can be harder to use |
|
Privacy |
Not as strong |
Very strong |
|
Maintenance |
Simple |
Needs more work |
|
User Experience |
Smooth |
Sometimes slow or tricky |
|
Security |
Good, but not perfect |
Best for sensitive data |
Some people say very secure phones feel “suffocating” because they are not as easy to use. If you want the best privacy, you may have to give up some comfort. If you want both, choose a phone that gives you good privacy and is still easy to use.
Note: The best encrypted phone is the one that fits your privacy needs and feels good to use.
You can pick from lots of encrypted phones. All of them help keep your information safe. Some phones use end-to-end encryption to protect your chats. Others have open-source apps so people can check for problems. Some phones have privacy dashboards or special chips for more safety. Here is what experts think is most important:
|
Feature |
Why It Matters |
|---|---|
|
End-to-end encryption |
Keeps your chats private |
|
Open source |
Lets you check for weaknesses |
|
Privacy dashboard |
Shows what data apps collect |
Choose a phone that works for your needs. If you own a business, you might want more features. Creative people may like phones with AI tools. People who use phones every day can pick ones with simple privacy settings. Watch for new things in mobile security. Your privacy depends on staying careful.
FAQ
What makes an encrypted phone different from a regular smartphone?
Encrypted phones use special tools to keep your calls and messages private. You get more safety for your data. Regular phones do not protect you as much.
Can you use popular apps on encrypted phones?
You can use lots of popular apps. Some encrypted phones limit which apps you can add. This helps keep your phone safe. Always check the app store before you buy.
How does encryption protect your privacy?
Encryption mixes up your information so only you and someone you trust can read it. Hackers cannot see your messages or files. You stay in charge of your data.
Are encrypted phones hard to use?
Most encrypted phones work like normal smartphones. You may see extra privacy settings or security tools. You can learn how to use them fast.
Do encrypted phones cost more than regular phones?
Encrypted phones usually cost more because they use special parts and software. You pay for extra privacy and security. Some models look fancy, too.








