
You live in a world where your business is always busy. Every phone call, message, and file has your data and privacy. Entrepreneurs like you need more than a simple smartphone. You want real protection for your information, not just words. Strong advanced encryption, good security, long battery life, and fast connection are important. Today’s technology needs a phone that matches your speed and keeps your secrets safe.
Key Takeaways
-
Pick phones with end-to-end encryption to keep things private. This means only you and people you trust can see your stuff.
-
Find phones that get security updates often. Companies like Google and Apple give updates for a long time. These updates help keep your phone safe from new dangers.
-
Get phones with strong hardware security, like security chips and biometric authentication. These things help protect your phone from hackers.
-
Think about phones with dual operating systems for more control. You can keep work and personal data apart. This keeps both safe and neat.
-
Always look for phones with tamper-evident designs and strong build. A tough phone can handle daily use and keep your data safe in hard situations.
Advanced Encryption Essentials
End-to-End Data Protection
You want your business data to be private. End-to-end data protection keeps your information safe the whole time. It protects your data from when you send it until it gets to the other person. Phones like Vertu, Agent Q, Quantum Flip, Google Pixel 9 Pro (with GrapheneOS), Bittium Tough Mobile 2C, and SYC™ encrypted phone use advanced encryption. They keep your messages, calls, and files safe. These phones use strong encryption protocols at every step. You can feel calm because only you and the person you trust can see your information.
On-Device Encryption Standards
You need phones that use military-grade encryption. Look at the table below. It shows features in top encrypted smartphones:
|
Feature |
Description |
|---|---|
|
Encryption Kernel |
INTEGRITY kernel keeps data safe and encrypted all the time. |
|
Secure Communication |
MONAX network lets you send encrypted voice, video, and data over a special network. |
|
Device Isolation |
Dual domain operations keep work and personal data apart and safe. |
|
Data Protection |
Virtual self-encrypting drive locks all data before saving it. |
|
Multi-Personality Support |
Devices let you use different security domains on one phone. |
Phones like Bittium Tough Mobile 2C and Vertu have these security features. You get strong protection for your business and personal data.
Evaluating Encryption Protocols
You want technology that checks everything. Zero-Trust principles help keep you safe. Here is how Zero-Trust helps entrepreneurs:
-
You get nonstop checking of security settings for every user and device.
-
The chance of a breach hurting your network goes down.
-
Only people who are allowed can see certain data, so your private information stays safe.
When you pick a phone, look for advanced encryption and Zero-Trust features. These tools help you protect your business and feel confident.
Secure OS and Firmware
Hardened Operating Systems
You want your phone to be safe from threats. Hardened operating systems like GrapheneOS add more protection. These systems help block hackers and keep your business safe. Some phones, like Bittium Tough Mobile 2C, have two operating systems. You can switch between work and personal profiles. This setup lets you choose what you need. You feel more in control and can get more done.
Tip: Dual OS phones let you keep work and personal things apart. You can protect your work data and still use your favorite apps on one phone.
Regular Security Updates
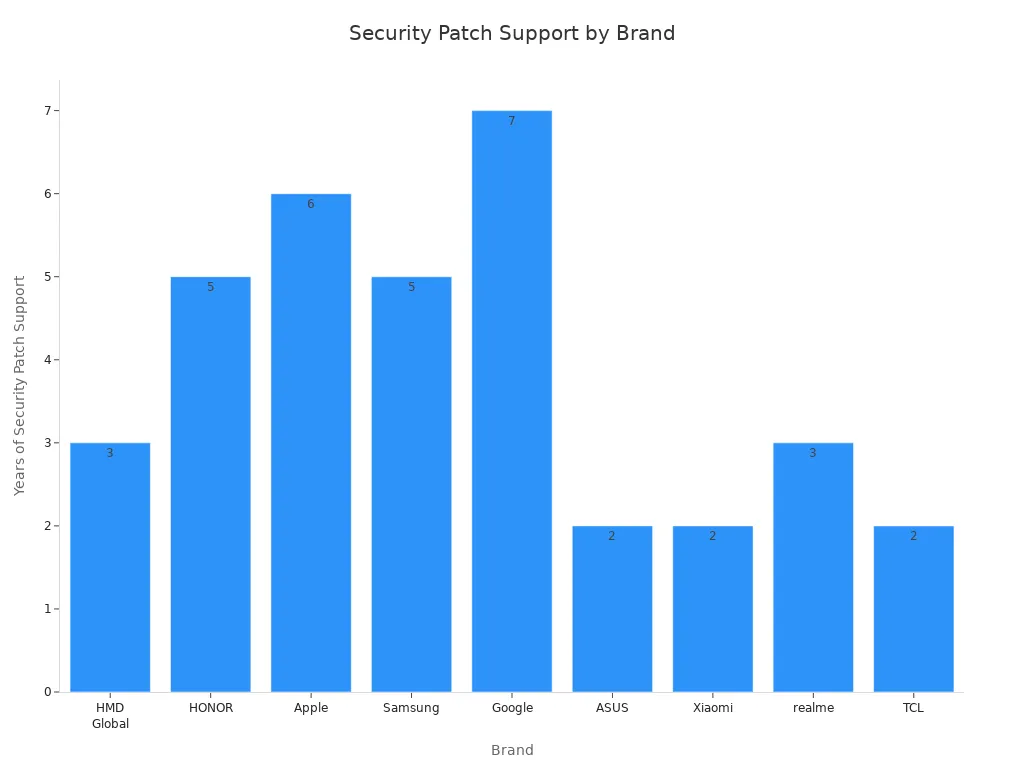
You need updates to stay safe from new dangers. Top brands give security patches often. These updates fix problems and keep your phone safe. Here is how long different brands support their phones:
|
Brand |
Security Update Commitment |
|---|---|
|
HMD Global |
2-3 years of security patches |
|
HONOR |
2 years of security patches, up to 5 for some models |
|
HUAWEI |
No firm commitment, case-by-case basis |
|
Apple |
At least 6 years of support |
|
Samsung |
4 upgrades and 5 years of patches |
|
|
7 upgrades and 7 years of security patches |
|
ASUS |
2 upgrades and at least 2 years of patches |
|
Xiaomi |
2 years of security patches |
|
realme |
2 upgrades and 3 years of patches |
|
TCL |
Up to 2 years of support, varies by price |
|
vivo |
No firm commitment, exceptions for X series |
Phones with non-rootable firmware are harder to change without your okay. You can relax because your device stays safe.
Permission Controls
You want to choose who can see your data. Permission controls let you set rules for each app and user. Here is how these controls help keep your data safe:
-
Authentication checks who you are with passwords or biometrics.
-
Authorization decides what you can do after you log in.
-
Limiting access means only the right people see private data.
-
Preventing unauthorized access keeps strangers out.
-
Monitoring and auditing show who looks at your data.
-
Following rules keeps your business legal.
-
Principle of Least Privilege gives users only what they need.
-
Protection against leaks hides private information.
-
Attribute-based access lets you control data by user details.
You get to control your phone’s security. Entrepreneurs need these features to keep business information safe and private.
Hardware Security Features

Security Chips and HSM
You want your phone to keep your business safe. Security chips and hardware encryption modules help with this. These small chips are inside your phone. They protect your data from cyberattacks. You can find them in top 5G phones and luxury brands like Vertu. More people want these chips now. The market is growing quickly. Cyberattacks have gone up by 38% each year. Banks and financial companies use hardware encryption much more now. They use it 120% more than before. You can feel calm because your information is locked at the hardware level.
-
Security chips block hackers from stealing your data.
-
Hardware encryption keeps your files safe, even if someone takes your phone.
-
More companies use these chips because they work better than software.
Biometric Authentication
You want to unlock your phone fast and safely. Biometric authentication lets you use your face, fingerprint, or eye. This makes it easy for you and hard for others. It works well with hardware encryption. You get strong protection. You do not need to remember long passwords. But no system is perfect. Some experts have fooled fingerprint and face scanners with masks or fake prints. So, you should use biometrics with other security features for the best safety.
Tamper Resistance
You need a phone that fights back if someone tries to break in. Tamper-resistant designs protect your device from attacks. Secure boot makes sure your phone only runs trusted software. Trusted execution environments (TEEs) add more hardware encryption. They keep your business data safe, even if the main system is hacked.
|
Role of TEEs in Hardware-Based Security for Business Smartphones |
Description |
|---|---|
|
Isolated Environment |
TEEs give a safe space for sensitive data. Your data stays safe even if the main OS is hacked. |
|
Secure Operations |
TEEs help with biometric authentication and encryption key management. These are important for keeping business data safe. |
|
Protection Against Threats |
TEEs keep sensitive information secure and tamper-resistant, even if there is malware. |
Tip: For the best protection, pick a phone with hardware encryption, security chips, and tamper-resistant features. These tools help entrepreneurs keep business secrets safe.
Encrypted Communications
Secure Messaging and Calls
You talk to people every day for work. Secure messaging and calls help keep your business safe. Phones like the SYC™ encrypted phone and Bittium use end-to-end encryption. Only you and the person you trust can read your messages or hear your calls. You do not need to worry about someone spying on you. These features help you work with your team in real time. You can talk to your team or clients without being scared. Your phone acts like a shield for your data.
Tip: Pick secure apps that let you make encrypted calls and send messages. They help keep your talks private and make teamwork better.
Encrypted Email and File Transfer
You send important files and emails often. You want your files and emails to be encrypted and safe. Many phones now have built-in encryption for emails and files. This keeps your business information safe from hackers. You can share documents with your team and know your data is safe. Good communication tools help you work with others easily. You do not waste time worrying about leaks. Your phone helps you work faster and smarter.
|
Feature |
Benefit |
|---|---|
|
Encrypted file storage |
Keeps files safe from hackers |
|
Secure email |
Protects business information |
|
Fast file transfer |
Supports collaboration |
Third-Party App Security
You use many apps for important business tasks. Not all apps keep your data safe. You should check app permissions and pick apps with strong encryption. Zero-Trust means you never think an app is safe without checking. You always make sure. This keeps your phone protected. Good app security helps your phone stay connected and saves battery. You get easy communication and better teamwork with trusted apps.
Note: Entrepreneurs who use secure apps and phones with strong encryption stay ahead. You protect your business and keep your team working together.
Physical Durability and Data Wipe
Tamper-Evident Design
You need a phone that shows if someone tampers with it. Tamper-evident design lets you spot problems quickly. Bittium Tough Mobile 2C meets military standards. This strong build protects your phone from damage and tough places. Vertu uses strong materials too, giving you more peace of mind. If you work in risky places, these features help keep your business safe. You can trust your phone to protect your data, even when things get hard.
Tip: Always look for tamper-evident seals or alerts on your phone. They help you know if someone tries to break in.
Water, Dust, Shock Resistance
You use your phone everywhere you go. Sometimes you drop it, spill water, or work outside. Phones like Bittium Tough Mobile 2C and Vertu can handle these things. They resist water, dust, and shocks, so accidents are not a big problem. This toughness means your phone keeps working in rough places. You stay connected, your battery lasts longer, and your business keeps going. Entrepreneurs need a phone that can handle daily life and keep data safe.
|
Feature |
Benefit |
|---|---|
|
Water resistance |
Stops damage from spills |
|
Dust resistance |
Blocks tiny particles |
|
Shock resistance |
Survives drops and bumps |
Secure Disposal
When you stop using your phone, you want your data to stay safe. Secure disposal is important for business safety. You should use special software to erase everything. Crushing or shredding hard drives makes sure no one can get your data. Some companies offer safe data destruction services. They take care of your phone and keep records of what they do. Teaching your team about secure disposal helps everyone stay careful. A good plan for destroying data keeps your business safe from leaks.
Note: Never throw away a phone before wiping the data. Secure disposal keeps your secrets safe and your business protected.
Ongoing Support and Brand Reputation
Manufacturer Security Commitment
You want a phone that keeps its promises. Some brands work hard to protect your device. Vertu makes luxury phones with strong security. Agent Q and Quantum Flip care about privacy for people who need it. Bittium and SYC™ make phones for tough jobs and safe places. Google Pixel 9 Pro uses GrapheneOS, which gets updates often. When you pick a phone, check if the brand talks about security. You need a company that cares about your privacy and keeps your phone safe.
Tip: Pick a brand that tells you about its security and fixes problems fast.
Long-Term Software Support
You want your phone to work for a long time. Software support helps your phone stay safe and run well. Some brands give updates for many years. Apple gives 5 to 7 years of big iOS updates. Samsung and Google Pixel give 7 years of updates. OnePlus gives 4 OS updates and 6 years of security patches. These updates help keep your business safe and your encryption strong.
|
Brand |
Average Software Support Duration |
|---|---|
|
Apple |
5-7 years of major iOS updates |
|
Samsung |
7 years of OS and security updates |
|
Google Pixel |
7 years of OS and security updates |
|
OnePlus |
4 OS updates and 6 years of security patches |
Phones with more support help you worry less. You do not have to fear losing safety or missing new features.
Evaluating Top Brands
You want to trust your phone brand. Vertu, Agent Q, Quantum Flip, Google Pixel 9 Pro, Bittium, and SYC™ all have strong security. Vertu is known for luxury and privacy. Agent Q and Quantum Flip focus on encryption and privacy tools. Google Pixel 9 Pro with GrapheneOS gets quick updates and good support. Bittium and SYC™ make phones for people who need safe calls and strong hardware. When you look at brands, see how often they update and if they care about your needs.
-
Pick brands that update their phones often.
-
See if the company listens to users and fixes things fast.
-
Choose a phone that fits your work and security needs.
Note: A trusted brand with good support helps you keep your business safe and your data private.
Choosing the Ultimate Smartphone for Entrepreneurs
Security Certifications
When you want the best phone for entrepreneurs, look for security certifications. These show your phone follows strict safety rules. Here are some you might see:
-
Common Criteria (CC): This checks if security features work well.
-
FIPS 140-2: This means your phone uses strong cryptography.
-
Mobile Device Management (MDM) Certifications: These help you manage devices safely.
-
ISO 27001: This keeps your business information secure.
-
Trusted Execution Environment (TEE) Certifications: These protect important actions on your phone.
Some certifications test your skills in mobile security too. Here is a quick chart:
|
Certification Name |
Cost |
Description |
|---|---|---|
|
Aruba Certified Mobility Expert (ACMX) |
$1200 |
Tests if you can design safe wireless networks. |
|
Certified Expert Mobile Security Professional (CEMP) |
$350 |
Shows you know how to keep app data safe. |
|
Credentialed Mobile Device Security Professional (CMDSP) |
$395 |
Proves you can manage and secure mobile devices. |
|
GIAC Mobile Device Security Analyst (GMOB) |
$1999 |
Checks if you can stop mobile threats. |
Balancing Usability and Security
You want a strong phone that keeps your data safe and is easy to use. Sometimes, security tools like multi-factor authentication and encryption make things harder. You need to find a good balance. Work with experts who know about business and cybersecurity. They help you set up strong protection that is not too hard to use. Good usability lets you focus on work and talking to others, not just security.
Tip: Try the phone before you buy it. Make sure you can use all the features easily.
Key Questions Before Purchase
Before you choose your phone, ask yourself these questions:
-
Does the battery last all day for your work?
-
Is the screen size good for you?
-
Can you pay for it, or is it too expensive?
-
Does it have enough memory for your apps and files?
-
Do you like the operating system?
-
Will the camera work for your business?
-
Does the design feel good in your hand?
-
Will it work with your favorite accessories?
-
Does it have fast internet?
Picking the right phone helps you stay connected and get more done. A strong phone gives you what you need to grow your business.
You know your phone is important for your business. Advanced encryption helps keep your data safe. There are millions of cyberattacks every year. Here are some facts:
|
Fact |
Value |
|---|---|
|
Mobile web traffic |
54% |
|
Average data breach cost |
Over $4 million |
Choosing a phone with strong security makes you more productive. It also helps your battery last longer. Two-factor authentication, biometric locks, and remote wipes are helpful. These features help entrepreneurs stay safe and ahead. Use this checklist to pick the best phone for your business.
FAQ
What makes a smartphone secure for entrepreneurs?
You need a phone with strong encryption and hardware security. Regular updates help keep your business data safe. These features protect your information from hackers and other threats.
How does advanced encryption improve productivity?
Advanced encryption lets you work without fear of leaks. You can send files and messages fast. This helps you focus on your work and get more done.
Can I use my secure phone for personal and business needs?
Yes! Many secure phones let you switch between profiles. You can keep your business private and still use your phone for fun.
What should I do before selling or recycling my phone?
Always erase your data with trusted software. Remove your accounts and reset your phone. This keeps your information safe when you get a new device.
Are secure phones hard to use?
No, most secure phones are easy to use. The menus are simple and controls are clear. You can turn on security features with just a few taps.








