
Looking for the most secure smartphones to protect your conversations in 2025? Here are the top picks you should know:
-
VERTU Quantum Flip Calfskin Series – Caramel Brown
-
Purism Librem 5
-
Blackphone PRIVY 2.0
-
Bittium Tough Mobile 2C
These models stand out as the most secure smartphones because they use hardware root of trust, system integrity checks, hardened operating systems, and frequent updates. You get secure communications, open-source transparency, and even hardware kill switches. Picking the best secure smartphones helps you keep your privacy and security strong. Online privacy matters more than ever, so choosing the most secure cell phone can make all the difference. With so many secure cell phones out there, you want the best encrypted phones that fit your needs. This secure smartphone range gives you peace of mind with the most secure cell phones on the market.
Key Takeaways
-
Choose smartphones with strong encryption, secure operating systems, and hardware kill switches to protect your conversations from hackers.
-
Regular software updates keep your phone safe by fixing security flaws and blocking new cyber threats.
-
Biometric security like fingerprint or face unlock adds fast and reliable protection for your device.
-
Pick a phone that fits your lifestyle and privacy needs, whether you want luxury, open-source control, or military-grade security.
-
Use encrypted apps, enable two-factor authentication, and avoid public Wi-Fi without a VPN to boost your phone’s security every day.
Key Security Features

Encryption
You want your conversations to stay private, right? Strong encryption makes that possible. With end-to-end encryption, your messages turn into unreadable code before they leave your phone. Only the person you send them to can unlock and read them. This means hackers, cyber criminals, or even internet providers can't see your sensitive data. Hardware encryption adds another layer, protecting your files and chats even if someone gets physical access to your device. If you use encrypted communications, you keep your secrets safe from prying eyes.
Tip: Always choose messaging apps that use end-to-end encryption for the most secure cell phone experience.
Secure OS
A secure operating system is the backbone of any privacy-focused smartphone. Systems like GrapheneOS and TAILS OS block unwanted tracking and keep your data protection strong. They remove risky apps, use sandboxing, and push frequent security updates. You get a safer environment for your sensitive data. Some secure OS options even use Tor to hide your online activity, making it tough for anyone to track you.
|
OS |
Security Focus |
Privacy Features |
|---|---|---|
|
GrapheneOS |
Hardened Android |
No Google, sandboxed apps |
|
TAILS OS |
Tor-based anonymity |
Wipes traces, encrypts data |
Hardware Kill Switches
Physical kill switches give you control over your phone’s camera, microphone, and radios. Flip a switch, and you instantly block hackers or cyber snoops from spying. Phones like the Librem 5 and Bittium Tough Mobile 2C use these switches to cut off hardware access. This feature stops malware and remote attacks cold, keeping your conversations private.
Regular Updates
You need regular updates to stay ahead of cyber threats. Updates fix bugs and patch security flaws before attackers can use them. If you ignore updates, you leave your device open to known risks. Installing updates keeps your security features fresh and your phone protected.
-
They improve security and usability
-
They help block new cyber attacks
Biometric Security
Biometric security uses your fingerprint or face to unlock your phone. It’s fast and hard to fake. These features make it tough for anyone else to access your device or apps. When combined with other security features, biometrics boost protection for your sensitive data. Just remember, you should always use strong encryption and data protection along with biometrics for the best results.
1. VERTU Quantum Flip Calfskin Series – Caramel Brown
Security Features
You want a phone that feels like a fortress. The VERTU Quantum Flip Calfskin Series – Caramel Brown gives you just that. This phone packs triple-layer quantum encryption, which means your conversations stay private. You get a sovereign security chip that guards your data like a digital bodyguard. The three-finger biometric key lets you wipe everything in seconds if you ever feel threatened. You can switch between three independent systems for work, life, and privacy. This setup gives you vault-like security for every part of your day. The phone even uses second-level data self-destruction, so your secrets stay safe, no matter what.
Pros and Cons
Pros:
-
Luxury design with calfskin and sapphire crystal
-
Foldable screen with King Kong rotating shaft for durability
-
Snapdragon 8 Elite Supreme Edition chip for fast performance
-
16GB RAM and 1TB storage for all your files
-
Two-way satellite communication for global coverage
-
Unhackable triple-layer encryption and biometric wipe
-
24/7 concierge service and exclusive perks
Cons:
-
Premium price may not fit every budget
Pricing
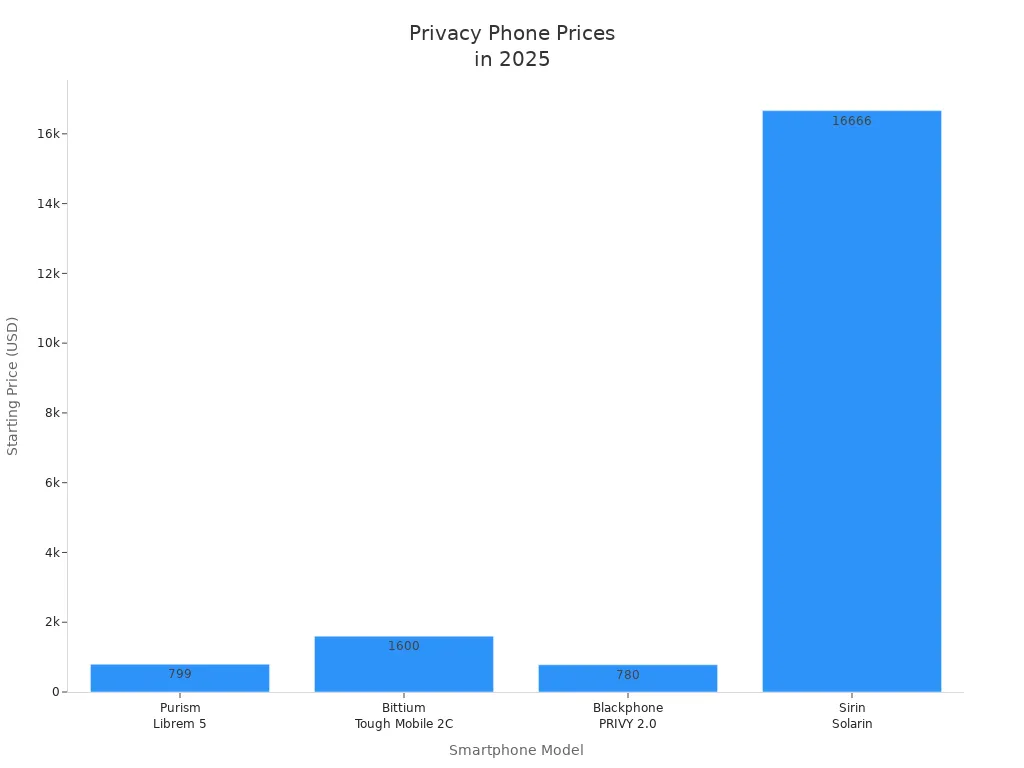
The VERTU Quantum Flip Calfskin Series – Caramel Brown comes in at $4,300. You pay for top-tier materials, advanced engineering, and a suite of secure features. If you want a phone that stands out and keeps your data safe, this price reflects the value.
Best For
You should pick this phone if you want the most secure experience and love luxury. It fits business leaders, privacy-focused professionals, and anyone who wants unhackable protection. If you travel often or handle sensitive information, this phone gives you peace of mind with its security features and vault-like security.
2. Purism Librem 5
Security Features
If you want a phone that puts you in control, the Purism Librem 5 stands out. This device gives you physical hardware kill switches, so you can turn off WiFi, Bluetooth, cellular, microphone, and camera with a simple flick. When you flip all the switches, you even disable GPS. You get PureOS, a fully open-source operating system that does not track you or send your data anywhere. The Librem 5 also separates the CPU from the cellular baseband, which helps block attacks that target your phone’s radio. You can run desktop apps like Firefox, giving you more control over your privacy. The phone supports lifetime security updates, so you stay protected for years.
|
Security Feature |
Description |
|---|---|
|
Hardware Kill Switches |
Physical switches that disconnect WiFi, Bluetooth, cellular signal, microphone, and camera; all switches also disable GPS. |
|
Operating System |
Runs PureOS, a fully free, ethical, open-source OS not based on Android or iOS, ensuring user control and no tracking. |
|
Ethical Supply Chain (Librem 5 USA) |
Made in USA electronics with strict oversight of component sourcing and manufacturing to prevent hardware backdoors. |
|
CPU and Cellular Baseband Separation |
The CPU is separated from the cellular baseband to enhance security against baseband attacks. |
|
Free Software Drivers |
Uses free software drivers (e.g., for GPU) to maintain transparency and security. |
|
IP-Native and Decentralized Communication |
Supports IP-native and decentralized communication by default, enhancing privacy. |
|
Lifetime Security Updates |
Provides ongoing security updates, privacy improvements, and bug fixes without performance compromise. |
|
Real Convergence |
Allows running desktop-class applications like desktop Firefox, improving security and user control. |
Pros and Cons
You want to know what works and what doesn’t. Here’s a quick look:
-
Pros:
-
You get true FOSS-compliant hardware and software.
-
The company focuses on customer interests as a Social Purpose Corporation.
-
-
Cons:
-
Some users report call audio issues.
-
Camera and Bluetooth may not always work.
-
Battery life can be short, so you might need extra batteries.
-
Power management and heat can be a problem.
-
Some proprietary firmware remains, despite open-source claims.
-
Company transparency has raised concerns.
-
Note: The Librem 5’s unique hardware kill switches and open-source OS make it a favorite for privacy fans, but you may face some trade-offs in daily use.
Pricing
You don’t have to break the bank for strong privacy. The Purism Librem 5 starts at $799, making it a mid-range option among secure smartphones. It costs less than high-end models like the Bittium Tough Mobile 2C and Sirin Solarin, but sits close to the Blackphone PRIVY 2.0.
Best For
Pick the Librem 5 if you want a secure phone with real hardware controls and an open-source system. This phone fits privacy advocates, tech enthusiasts, and anyone who wants an unhackable device with lifetime updates. If you value user control and transparency, this phone gives you peace of mind.
3. Google Pixel 8 with GrapheneOS
Security Features
You want a phone that feels truly secure. The Google Pixel 8 with GrapheneOS gives you a modified os for elite security. When you install GrapheneOS, you get advanced sandboxing and exploit protection that goes beyond regular Android. Your device uses verified boot, which checks for tampering every time you turn it on. You get a hardened browser called Vanadium, which blocks risky scripts and keeps your web activity untraceable. The system disables device identifier leaks, so apps and websites cannot track you easily. You can manage user profiles and log out securely, wiping encryption keys for extra privacy. GrapheneOS also blocks unnecessary radios and services, shrinking the attack surface. You get hundreds of security patches and the latest Linux kernel updates, so your phone stays protected.
Tip: You can use the Auditor app to check your device’s integrity and monitor for threats.
Pros and Cons
Pros:
-
Pixel hardware gives you timely firmware and software updates.
-
Titan M2 chip and verified boot protect against insider attacks.
-
USB port controls help block physical hacking attempts.
-
Sandboxed Google Play lets you use apps without giving up security.
Cons:
-
Some hardware parts use proprietary code you cannot replace.
-
Google services, even sandboxed, may still send data to Google.
-
Cell tower tracking and hardware backdoors are risks outside OS control.
Pricing
You want value for your money. The Pixel 8 with GrapheneOS costs more upfront than some other secure phones, but you get at least seven years of security updates. That means you spend less over time. You can save by choosing the Pixel 8a or waiting for sales. Used Pixel models like the 6a offer good security at a lower price. Here’s a quick look:
|
Aspect |
Pixel 8 with GrapheneOS |
Other Secure Phones |
|---|---|---|
|
Security Update Longevity |
2-5 years |
|
|
Hardware Security |
Titan M2, Verified Boot |
Varies |
|
Cost |
Premium, but long-term value |
Varies |
Best For
Pick the Pixel 8 with GrapheneOS if you want a secure phone that stays untraceable and up-to-date for years. This phone fits privacy-conscious users, tech enthusiasts, and anyone who wants a modified os for elite security without giving up app compatibility. If you want strong protection and easy updates, this device is a smart choice.
4. Samsung Galaxy S23 Ultra
Security Features
You want a phone that keeps your conversations private and your data safe. The Samsung Galaxy S23 Ultra gives you a strong set of security tools right out of the box. Here’s a quick look at what you get:
|
Security Feature |
Description |
|---|---|
|
End-to-End Encrypted Messaging |
Messages app uses encryption so only you and your contact can read your chats. |
|
Encrypted Video Calls |
Video calls stay confidential, blocking eavesdroppers. |
|
Biometric Authentication |
Face recognition and ultrasonic fingerprint scanning keep your device locked to strangers. |
|
Secure Folder |
Store your sensitive files and apps in a digital vault, protected by password or biometrics. |
|
Knox Security Platform |
Multi-layered protection and real-time threat detection guard against malware and unauthorized access. |
|
Enhanced Privacy Controls |
Manage app permissions and see what data apps use with a privacy dashboard. |
|
Secure Wi-Fi |
Protects your connection on public networks, making it harder for hackers to snoop. |
|
Samsung Pass |
Use biometrics to log in to apps and websites safely. |
You also get built-in vpns support, which helps keep your online activity untraceable when you browse or message.
Pros and Cons
Pros:
-
You get a secure phone with advanced encryption and real-time threat detection.
-
Biometric security makes unlocking fast and safe.
-
Secure Folder and privacy controls give you extra peace of mind.
-
The S23 Ultra supports built-in vpns for safer browsing.
Cons:
-
Some features depend on Samsung’s software updates.
-
Not all privacy tools are enabled by default, so you need to set them up.
Tip: Set up your Secure Folder and privacy dashboard right away to get the most protection.
Pricing
You can find the Samsung Galaxy S23 Ultra for about $600 if you buy a renewed model from third-party sellers. Refurbished options may cost even less. When it first launched, the price was around $1200. Now, you get flagship features and strong security at a much lower price. This makes the S23 Ultra a smart pick if you want premium features without breaking the bank.
Best For
Pick the S23 Ultra if you want a secure phone that feels familiar and powerful. It fits business users, students, and anyone who wants strong privacy tools without switching to a niche device. If you want an untraceable experience with built-in vpns and easy-to-use security, this phone is a great choice.
5. Blackphone PRIVY 2.0
Security Features
You want a phone that puts privacy first. The Blackphone PRIVY 2.0 gives you a heavily modified Android OS with enhanced security. You get end-to-end encryption for calls and messages using the ZRTP protocol. The device blocks Google services, so you avoid unwanted tracking and data leaks. You can use the Silent Phone app for encrypted voice and messaging. The phone protects you from SIM swap attacks, keeping your cellular identity safe. You also get a secure boot system that only lets authorized software run. If you lose your phone, you can wipe your data remotely. The PRIVY Chat and PRIVY Vault apps help you store messages and files with vault-like security.
|
Description |
|
|---|---|
|
End-to-end encryption (ZRTP protocol) |
Secure calls and messages with strong encryption protocol |
|
Modified Android OS |
Enhanced security features built on Android platform |
|
Blocking Google services |
Prevents tracking and data leaks by disabling Google services |
|
Secure boot system |
Ensures only authorized software runs on the device |
|
Remote wipe |
Allows erasing user data remotely if device is lost or stolen |
|
No pre-installed bloatware |
Reduces potential security vulnerabilities |
|
Silent Phone app |
Provides encrypted voice and messaging communications |
|
Protection against SIM swap attacks |
Guards against unauthorized SIM card changes |
|
PRIVY Chat and PRIVY Vault |
Secure applications for encrypted messaging and secure data storage |
Pros and Cons
You want to know if this phone fits your needs. Here’s a quick look:
|
Aspect |
Advantages |
Disadvantages |
|---|---|---|
|
Security Features |
Hardened permissions, theft protection, end-to-end encrypted calls & video |
Modest hardware specs, limited as an all-round smartphone |
|
Communication |
Uses Silent OS and Silent Phone app with ZRTP encryption |
Subscription model required, potentially costly ($825 to $2540) |
|
Target User |
Ideal for users primarily concerned with wiretapping and communication secrecy |
Not suitable for users needing versatile smartphone functionality |
-
You get secure databases and apps for data protection.
-
The phone is perfect if you care about privacy and want strong protection for your conversations.
-
You may find the hardware less powerful than other flagship phones.
Tip: If you want maximum privacy, use PRIVY Vault for your sensitive files.
Pricing
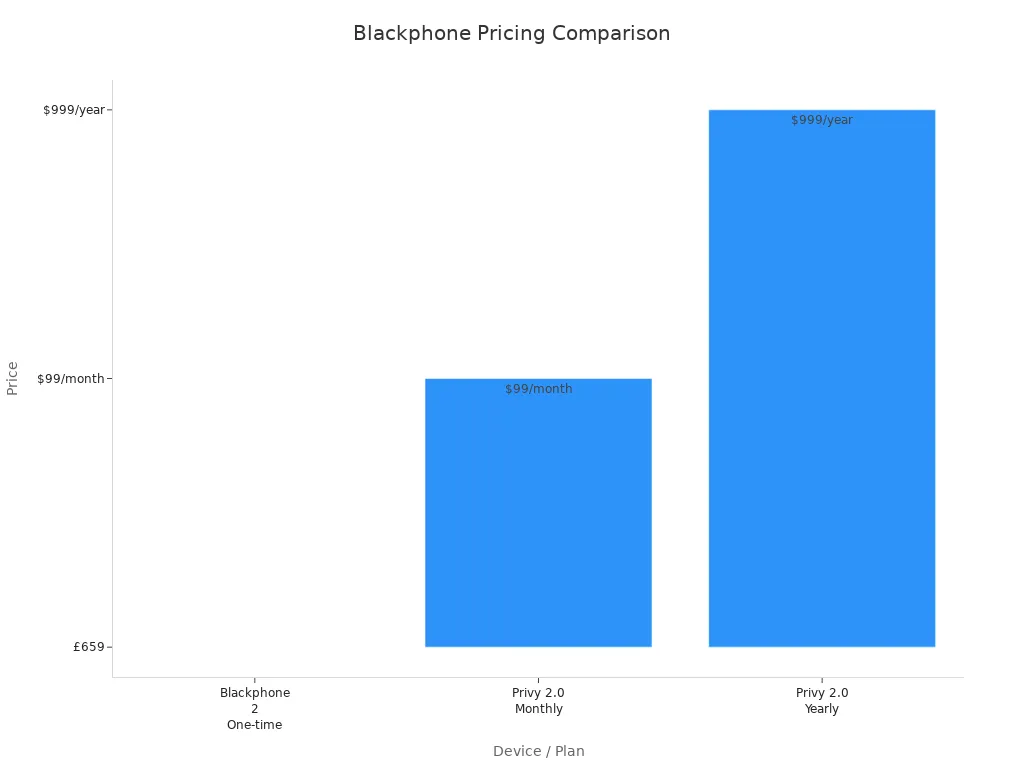
You want to know the cost before you decide. The Blackphone PRIVY 2.0 uses a subscription model. You can pay $99 per month for unlimited talk, text, global high-speed data, SIM security, and $5M insurance. If you prefer a yearly plan, you pay $999 per year and get a 60-day money-back guarantee. This pricing is higher than some other secure phones, but you get extra privacy features and insurance.
Best For
Pick the Blackphone PRIVY 2.0 if you want secure communication and vault-like security for your data. This phone works best for journalists, activists, and anyone who needs to keep conversations private. If you want a device focused on privacy and don’t need lots of extra features, this phone is a smart choice.
6. Bittium Tough Mobile 2C
Security Features
You want a phone that can handle anything. The Bittium Tough Mobile 2C brings military-grade protection to your pocket. This device uses a dual-boot system, letting you switch between a hardened Bittium Secure OS for confidential work and a secure Android 11 for personal use. You get AES-256 and RSA encryption for all your data, even on your memory card. The phone has a dedicated secure element chip for key storage and a backup battery for tamper monitoring.
Here’s a quick look at what you get:
|
Security Feature Category |
Details |
|---|---|
|
Operating Systems |
Dual-boot: Bittium Secure OS (CONFIDENTIAL) & Hardened Android 11 |
|
Encryption |
AES-256, RSA, secure element chip |
|
Physical Security |
MIL-STD-810G ruggedness, IP67 water resistance, tamper-evident seals |
|
Privacy Mode |
Hardware switch disables microphones, cameras, Bluetooth |
|
Authentication |
Two-factor (YubiKey 5 NFC), biometrics, strong passwords |
|
Communication Security |
Always-on VPN, end-to-end encrypted calls and messages |
|
Remote Management |
Remote wipe, audit logs, application whitelisting |
|
Certifications |
CONFIDENTIAL (NCSA-FI, TL III), NATO Restricted |
You also get a special privacy mode that blocks microphones and cameras, so no one can spy on you.
Pros and Cons
-
Pros:
-
Super tough design for drops and water.
-
Dual operating systems for work and personal life.
-
Certified for government and NATO use.
-
Emergency data wipe switch for instant protection.
-
Always-on VPN and secure calls.
-
-
Cons:
-
Bulkier than regular smartphones.
Tip: If you need a phone for high-security environments, this one stands out.
Pricing
You can expect to pay between $1,500 and $2,000+ for the Bittium Tough Mobile 2C. This price is higher than phones like the Librem 5 or Sirin Labs Finney U1, but you get advanced security, rugged hardware, and government-level certifications. The cost reflects its focus on professional and secure environments.
Best For
Choose the Bittium Tough Mobile 2C if you work in government, law enforcement, or any job where security matters most. This phone fits professionals who need a secure device that can survive tough conditions and keep sensitive information safe. If you want peace of mind and top-level protection, this phone delivers.
7. Sirin Labs Finney U1
Security Features
You want a phone that takes privacy and crypto security to the next level. The Sirin Labs Finney U1 does just that. This device stands out with its blockchain-based features and strong protection for your digital assets. Here’s what you get:
-
An embedded cold storage wallet keeps your cryptocurrencies offline, away from hackers.
-
A dedicated security switch lets you disconnect from the internet, creating an air gap for extra privacy.
-
Tamper-resistant hardware helps stop anyone from physically breaking into your phone.
-
Decentralized authentication and advanced encryption algorithms protect your identity and assets.
-
The phone uses blockchain technology for transaction security, transparency, and immutability, so you don’t have to worry about centralized data breaches.
Tip: If you hold crypto, you’ll love how the Finney U1 keeps your coins safe and your conversations private.
Pros and Cons
You want to know if this phone fits your needs. Here’s a quick look at what makes the Finney U1 shine—and where it might fall short:
|
Pros |
Cons |
|---|---|
|
Unique cold storage wallet integrated into the phone |
Cold wallet screen is fiddly and not user-friendly |
|
Highly secure customized Android OS (Sirin OS) with extensive cybersecurity features |
Average camera quality |
|
Comprehensive cryptocurrency tools aimed at experienced users |
Limited appeal for casual or new cryptocurrency users |
|
Distinctive design |
High price tag |
|
Suitable for users already invested in cryptocurrency |
Hardware and software are somewhat dated |
|
Strong security features including intrusion protection and network attack protection |
Limited ecosystem for spending cryptocurrency, reducing practical use |
Pricing
You can expect to pay around $999 for the Sirin Labs Finney U1. This price puts it in the premium range, but you get a secure phone with unique crypto features. If you want a device that protects your digital assets and private chats, the cost reflects the advanced technology inside.
Best For
Pick the Finney U1 if you’re a cryptocurrency enthusiast who wants a secure phone for both digital assets and private conversations. This device works best for experienced crypto users who value privacy and need built-in tools for managing coins. If you want a phone that stands out and keeps your crypto safe, the Finney U1 is a smart choice.
Best Encrypted Phones Comparison

Feature Matrix
You want to find the best encrypted phones without digging through endless specs. This table makes it easy. You can see how the most secure smartphones stack up on security features, price, and who should use them. Just scan the rows to spot the best secure smartphones for your needs.
|
Smartphone |
Security Features |
Pricing |
Best For |
|---|---|---|---|
|
VERTU Quantum Flip Calfskin Series |
Triple-layer quantum encryption, sovereign security chip, biometric wipe, satellite comms |
$4,300 |
Luxury seekers, business leaders, world travelers |
|
Purism Librem 5 |
Hardware kill switches, open-source OS, CPU/baseband separation, lifetime updates |
$799 |
Privacy advocates, tech enthusiasts |
|
Google Pixel 8 with GrapheneOS |
Hardened OS, verified boot, sandboxed apps, Titan M2 chip, 7 years of updates |
$699+ |
Users wanting long-term security and updates |
|
Samsung Galaxy S23 Ultra |
Knox platform, Secure Folder, biometric security, privacy dashboard, built-in VPN |
$600+ (renewed) |
Mainstream users, business professionals |
|
Blackphone PRIVY 2.0 |
End-to-end encrypted calls/messages, SIM swap protection, secure boot, remote wipe |
$99/mo or $999/yr |
Journalists, activists, secure communication |
|
Bittium Tough Mobile 2C |
AES-256 encryption, dual OS, tamper-proof, NATO standards, privacy mode |
$1,500+ |
Government, military, high-security sectors |
|
Sirin Labs Finney U1 |
Cold storage wallet, security switch, blockchain tech, tamper-resistant hardware |
$999 |
Crypto users, digital asset managers |
Tip: If you want the best encrypted phones for private conversations, look for features like hardware kill switches, secure OS, and strong encryption. These features make secure cell phones stand out from the rest.
You can use this table to match your needs with the right phone. Some phones focus on luxury and style, while others give you military-grade protection. The most secure smartphones offer a mix of strong encryption, regular updates, and special privacy tools. Pick the one that fits your lifestyle and keeps your conversations safe.
Secure Mobile Phone Tips
Want to make your phone even safer? You can boost your privacy and security with a few simple steps. Here are some easy tips for increasing security and privacy on any device.
Use Encrypted Apps
Pick apps that use end-to-end encryption for your messages and calls. These apps turn your words into code, so only you and the person you contact can read them. Try Signal or WhatsApp for secure communications. You can also use apps that support encrypted phone calls to keep your chats private.
Tip: Always check if your app offers end-to-end encryption before you share sensitive data.
Enable Two-Factor Authentication
Turn on two-factor authentication (2FA) for your accounts. This adds a second step when you log in, like a code sent to your phone. Even if someone gets your password, they cannot get in without the code. You get comprehensive protection for your accounts.
Update Regularly
Keep your phone and apps up to date. Updates fix bugs and patch holes that hackers use. When you update, you help with protecting against cyber threats. Set your phone to update automatically if you can.
Avoid Public Wi-Fi
Public Wi-Fi can be risky. Hackers often use these networks to steal sensitive data. If you must use public Wi-Fi, turn on a vpn. This tool scrambles your data and keeps it safe from cyber snoops.
Review Permissions
Check what permissions your apps have. Some apps ask for more access than they need. Remove permissions that do not make sense. This step helps with data protection and keeps your information private.
Remember: Small changes can make a big difference in your phone’s security.
You have seen the top picks for the most secure smartphones in 2025. Each one stands out for strong privacy features and unique protection. To choose the best secure phone for you, think about your daily needs and how much privacy matters.
-
Pick a phone that matches your lifestyle.
-
Use safe habits like updating your device and using encrypted apps.
Stay alert for new threats and updates. Your privacy depends on it!
FAQ
What makes a smartphone truly secure?
A secure smartphone uses strong encryption, a secure operating system, and regular updates. It may also have hardware kill switches and biometric locks. These features help keep your conversations and data safe from hackers.
Can I make any phone more secure?
Yes! You can use encrypted apps, set up two-factor authentication, and update your phone often. Always review app permissions. These steps boost your privacy, even if your phone is not a special secure model.
Do secure phones work with regular apps?
Most secure phones support popular apps, but some limit access to protect your privacy. You may need to use open-source or privacy-focused alternatives for messaging, browsing, and email.
Are secure smartphones worth the price?
If you handle sensitive information or value privacy, a secure phone is a smart investment. You get peace of mind knowing your conversations and data stay protected.
How do hardware kill switches help?
Hardware kill switches let you turn off your phone’s camera, microphone, or radios with a simple flick. This stops hackers from spying on you, even if malware tries to take control.






