Comparing Network Security: 4G vs 5G Phones
Explore key network security differences between 4G and 5G phones.
Features | 4G Phone | 5G Phone |
|---|---|---|
Authentication Protocol | Uses EPS-AKA with symmetric keys | Multiple methods, unified framework |
Identity Protection | Permanent ID sent in clear text | Permanent ID always encrypted |
Network Architecture | Centralized core network | Service-based, modular core |
Encryption Strength | AES with 128-bit keys | AES with 256-bit keys |
Privacy Measures | Temporary IDs with flaws | Temporary IDs change each session |
Network Slicing | Not supported | Supports isolated virtual networks |
Vulnerability Risks | Legacy flaws, IMSI catchers | New API risks, IoT threats |
User Impact | Higher risk of tracking | Better privacy and protection |
Transition Security | Susceptible to downgrade attacks | Stronger but mixed risks remain |
5G phones have better network security than 4G phones. They use stronger authentication and encryption. Most people still use 4G networks, about 69%. Only 17% of people use 5G networks. Standalone 5G brings cloud-native technology and new protocols. These changes help fix old problems found in 4G. Network security is important. Weak protection on phones has caused many data breaches. Users should know about authentication and vulnerabilities. The switch from 4G to 5G affects privacy and safety. 5G makes things better, but some problems still exist when picking a phone.
Key Takeaways
5G phones have better security than 4G phones. They use stronger encryption and hide user identities. This helps keep your privacy safe.
5G networks use flexible designs like network slicing. They also use advanced authentication. These features lower risks and help stop attacks.
Moving between 4G and 5G can make security gaps. It is important to keep your devices updated to stay safe.
Users should pick devices with strong security features. They should also use strong passwords and update their devices often.
Even with better security, 4G and 5G still have cyber threats. Staying informed and careful helps protect your data.
5G vs 4G Network Security
Key Differences
4G and 5G networks are built in different ways.
4G networks have a main core called the Evolved Packet Core. Attackers can focus on this main area.
5G networks use a spread-out core called the 5G Core Network. This setup uses Service-Based Architecture. It breaks the network into smaller parts. This makes the network more flexible and harder to attack.
5G has new security features that 4G does not.
5G hides subscriber identifiers before sending them. This keeps user privacy safe and stops tracking. 4G sometimes sends these without hiding them.
5G uses the same protocols like HTTP/2 with TLS for safe communication. 4G uses different signaling protocols. This can make weak spots.
5G allows network slicing. The network can make separate virtual networks for different things. Each one has its own security rules. 4G cannot do this.
5G adds new security functions like the Authentication Server Function and Security Anchor Function. These help keep serving and home networks apart. This lowers the risk of spoofing.
The table below shows how 4G and 5G handle encryption and authentication:
Aspect | 4G (EPS-AKA) | 5G (5G-AKA, EAP-AKA', EAP-TLS) |
|---|---|---|
Authentication Protocol | EPS-AKA, symmetric keys | Multiple methods, unified framework |
Permanent Identity Protection | Sent in clear text | Always encrypted |
Authentication Decision Authority | Serving network | Home network entity AUSF |
Key Hierarchy | Shorter, fewer keys | Longer, more separation |
Support for Non-USIM Devices | Not supported | Supported |
Network Architecture | Centralized core | Service-based, modular |
Privacy Enhancements | Temporary IDs, flaws | Permanent ID always encrypted |
Flexibility | Limited | Open framework, multiple methods |
5G also makes radio access better with improved OFDMA and massive MIMO. These upgrades help with connection and reliability. They make attacks harder.
User Impact
Moving from 4G to 5G changes how users see network security.
5G gives stronger encryption and authentication. This means users get better protection for their data and identity.
Privacy is better because 5G hides user identifiers before sending them. Attackers cannot track users as easily as on 4G.
Network slicing in 5G lets operators make separate virtual networks. This lowers the chance of breaches and keeps important information safer.
Users get faster speeds and better connections with 5G. These upgrades help more devices, like smart home gadgets and IoT products. But more devices mean more places for attacks. Cyber threats can grow as more devices connect.
5G networks use smart security tools like AI-driven threat detection. These tools help find and stop attacks fast.
Zero-trust security models in 5G check users and devices all the time. This makes it harder for attackers to get in.
Network operators help keep users safe. They handle authentication, watch for threats, and use tools like deep packet inspection and DDoS protection. Operators also work with cloud and security service providers to keep the network safe.
What users do matters for network security on both 4G and 5G devices.
Users who trust their network and know about safety features use 5G more safely.
Using multi-factor authentication and strong passwords helps protect devices.
As 5G grows, some users use public Wi-Fi, which is less safe. This can let cyber threats like data interception and phishing happen.
Switching to new wireless brings strong security, but users must watch out for risks. Moving from 4G to 5G makes networks more complex and can leave gaps if old devices or networks are not updated.
Users with old phones may face more risks during the switch.
Telecom operators should remove old hardware and teach users about new security features.
Network Security Basics
Authentication
Authentication is very important for both 4G and 5G mobile networks. It helps devices and networks make sure they are talking to the right person. In 4G, a method called EPS-AKA is used. This method uses secret keys in the SIM card and the network. 5G makes this better by using more advanced protocols like 5G-AKA and EAP-TLS. These new protocols work with more types of devices, even ones without SIM cards.
The main ideas of authentication in mobile networks are:
Mutual Authentication: The device and the network check who each other are. This step helps stop fake base stations from tricking people.
Protection of User Identity: Devices do not send their real identity in plain text. They use encrypted or fake names instead.
Use of Secret Keys: Every user has special secret keys. The network and device use these to make safe session keys.
Secure Channels: After checking, the network makes encrypted channels to keep data safe.
Binding Security Relationship: The network links the device’s name and keys to make a safe connection.
Replay Protection: Sequence numbers stop attackers from using old messages again.
5G networks add new things like AUSF and SEAF to split up authentication jobs. This makes it harder for attackers to trick the system, especially when users move between networks.
Identity Protection
Identity protection is a big difference between 4G and 5G. In 4G, the device sends its real name, called IMSI, without hiding it at first. Attackers can catch this and follow users. This problem puts user privacy in danger.
5G fixes this with some upgrades:
The device hides its real name (SUPI) before sending it. It uses a special name called SUCI, which keeps the real name secret from attackers.
5G uses AUSF and SEAF, which split up authentication between the home and serving networks. This setup lowers the risk of spoofing.
5G lets new authentication methods like EAP-TLS work for IoT and private networks.
When users travel, 5G always lets the home network decide on authentication. This follows a zero-trust rule, making it safer than 4G, where the visited network decides.
Tip: Users who want better privacy should pick devices that work with 5G. The new identity protection in 5G makes it much harder for attackers to track or steal user information.
Both 4G and 5G try to give strong network security, but 5G has better tools to protect user identity and data.
4G Security Features
Encryption
4G networks use strong encryption to keep user data safe. Data moves between devices and cell towers. The main goal is to stop cyber threats and data breaches. 4G uses different encryption standards for this job. The table below lists the main algorithms and their roles in 4G security:
Encryption Standard / Algorithm | Purpose / Role in 4G LTE Security | Additional Details |
|---|---|---|
AES (Advanced Encryption Standard) | Encrypts data sent between devices and cell towers | Supports 128, 192, 256-bit keys; works in hardware and software |
SNOW 3G stream cipher | Replaces KASUMI for confidentiality | Used with UEA2 confidentiality algorithm |
UEA2 confidentiality algorithm | Keeps data private in 4G LTE | Replaces UEA1 used in 3G |
UIA2 integrity algorithm | Checks data integrity | Comes after UIA1 from 3G |
KASUMI block cipher | Used in 3G networks | Weaknesses led to replacement in 4G |
4G encryption mostly protects the radio link. It does not give end-to-end encryption. For full safety, users add protocols like SSL/TLS or VPNs. AES is a popular block cipher. It supports different key lengths and works in hardware and software. Key management is very important. Keys are kept in secure places and shared safely. Data is split into blocks and encrypted before sending. This helps stop breaches by making stolen data hard to read without the right keys.
Note: 4G encryption is strong, but 5G networks have even better encryption and privacy features.
Vulnerabilities
4G networks are safer than older ones, but they still have risks. These problems can cause breaches or let cyber criminals attack. Some common vulnerabilities in 4G are:
Location tracking: Attackers use signaling protocols to find where users are. This can lead to stalking or unwanted watching.
SS7 attacks: 4G uses the Diameter protocol, but some old SS7 problems remain. Attackers can listen to calls, read messages, or get past two-factor authentication.
Distributed Denial of Service (DDoS) attacks: Cyber criminals send lots of traffic to the network. This can stop service for many users.
IMSI catchers: These devices act like real cell towers. They steal communications and track users without them knowing.
The Diameter protocol handles authentication and authorization in 4G. It was made to be safer than SS7, but it still has weaknesses. Attackers can use these flaws, so Diameter is a worry for network operators. 4G networks face threats from old and new attack methods. More devices mean more chances for cyber attacks and breaches.
4G networks have fewer tools to find and stop these threats than 5G. 5G brings smarter security systems and better privacy protections. Users who want the best security should look at how 4G and 5G deal with vulnerabilities and cyber threats.
5G Security Features
Advanced Encryption
5g technology uses stronger encryption than 4G. The 5g network uses AES with 256-bit keys. 4G only uses 128-bit keys. This makes it harder for hackers to get user data. Privacy is better too. 5g uses temporary identifiers that change every session. This makes tracking users much harder. Network slicing in 5g creates separate virtual networks. If one slice is attacked, the others stay safe. The table below shows how 4G and 5g compare in encryption and privacy:
Feature | 4G Implementation | 5G Implementation and Advancements |
|---|---|---|
Encryption Protocol | AES with 128-bit keys | AES with 256-bit keys, providing stronger encryption |
Authentication Framework | EPS-AKA | 5G-AKA with two-factor authentication; also supports EAP-AKA’ and EAP-TLS, offering multiple authentication methods |
Privacy Measures | Static identifiers | Temporary identifiers that change per session, enhancing user privacy |
Network Architecture Security | N/A | Network slicing enabling isolated virtual networks to contain breaches |
Mutual Authentication | Limited | Mutual authentication at multiple communication layers to prevent man-in-the-middle attacks |
IoT Security | Basic security | Built-in protocols for secure boot, identity management, and secure firmware updates |
Authentication Upgrades
5g technology makes authentication better in many ways. The 5g network uses new protocols like 5G-AKA, EAP-AKA’, and EAP-TLS. These give mutual authentication between users and the network. User identity is safer with Subscriber Concealed Identity (SUPI). This hides real identity data from attackers. Key separation in 5g keeps signaling and user data more secure. The Security Edge Protection Proxy (SEPP) protects roaming and network communication. The new authentication system works for more things, like IoT devices and fast mobile internet. These upgrades help stop fraud, spoofing, and unwanted access. They also keep user identity and data private.
New Vulnerabilities
5g has strong security, but it brings new risks too. The speed and complexity of 5g make more problems possible. DDoS attacks have gone up by 200% since 2021. Many IoT devices on 5g do not have strong security. This lets hackers attack networks more easily. Data breaches happen faster, and ransomware spreads quickly. Supply chain attacks target third-party vendors in 5g systems. Edge computing brings new risks because attackers can target devices near users. The chart below shows how different threats have grown in 5g networks:
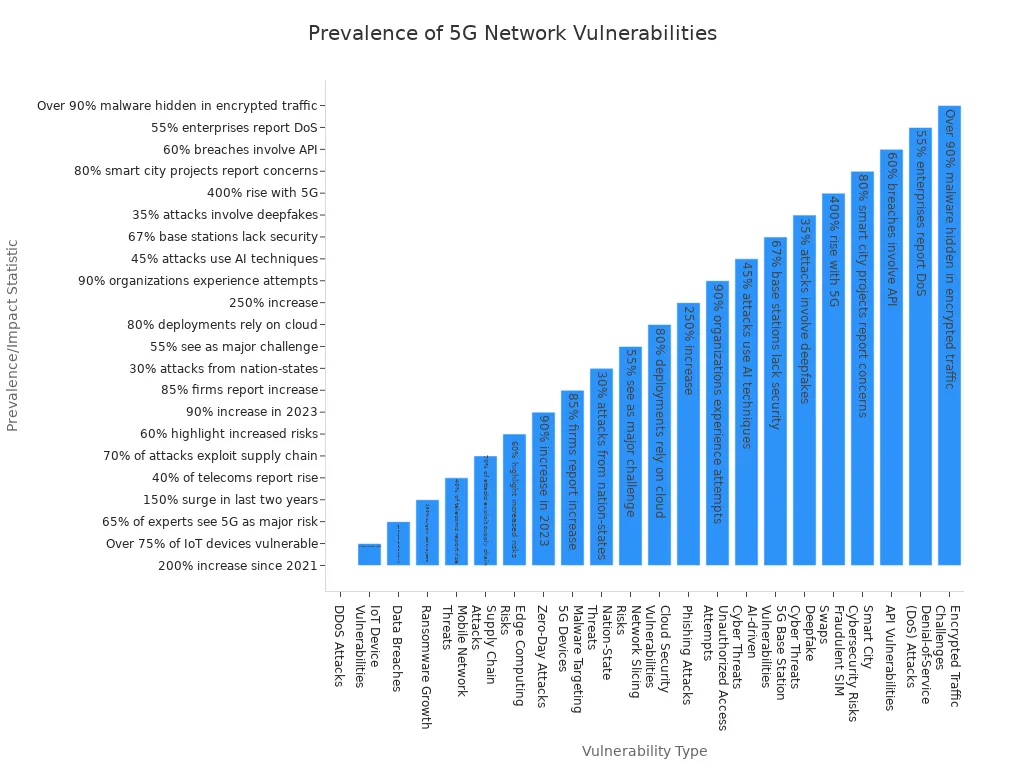
5g networks also have risks from bad API setups, cloud mistakes, and old 4G parts. Attackers use AI to make cyber attacks faster and find new weaknesses. Smart city projects and base stations in 5g need better protection. As 5g grows, users and companies must watch for new threats and keep security updated.
Bandwidth and Security
5G Bandwidth Benefits
5g gives much more bandwidth than 4G. This means users get faster downloads and streaming. Gaming is quicker too. People can download big files in seconds with 5g. The network supports more devices at the same time. This helps in crowded places. Low latency in 5g makes video calls smoother. Online games work better too. Businesses use 5g to run smart devices and sensors. They get better network performance. The table below shows how 4G and 5g compare in speed and bandwidth:
Feature | 4G | 5G |
|---|---|---|
Max Bandwidth | Up to 100 Mbps | Up to 10 Gbps |
Typical Speed | 10-50 Mbps | 100 Mbps – 1 Gbps |
Device Support | Thousands | Millions |
Latency | 30-50 ms | 1-10 ms (low latency) |
With 5g, users get faster speeds and better network performance. Streaming, cloud gaming, and smart home devices work better. The network can handle more connections without slowing down.
Security Implications
The big jump in bandwidth with 5g brings new security problems. Faster data speeds mean attackers can act more quickly. Hackers use cheap tools to reach more targets. More devices connect to 5g, so there are more places to attack. Many IoT devices on 5g have weak spots. Some send data without encryption. This makes it easier for hackers to get in.
5g's fast speeds and many connections give attackers more ways in.
More IoT devices mean bigger risks for DDoS attacks.
5g's complex setup, like network slicing and edge computing, brings new problems.
If one network slice is not safe, others can be hurt too.
Edge computing handles data close to users, but this also gives attackers more chances.
5g gives speeds that are 100 times faster and connects millions of devices. These changes make it harder to keep the network safe. New hardware and software can have weak spots. To protect users, experts say to use strong encryption and split up the network. Access controls and constant monitoring help too. AI and machine learning can find and stop threats faster. 5g makes security better, but more bandwidth means users and companies must watch out for new risks.
4G to 5G Transition

Transition Risks
Moving from 4G to 5G brings new security problems. Many devices still use 4G while trying 5G features. This mix creates risks because old 4G systems have known weak spots. Attackers look for these weak spots during the switch to 5G. They use downgrade attacks to make devices go back to 4G. This can lead to IMSI-catcher attacks and people getting in without permission.
When devices move between 4G and 5G, risks go up. 5G has stronger encryption and better authentication. But old 4G protocols still need support, so some weak spots stay. Attackers can find gaps and cause data breaches. More breaches happen when users do not update their devices or software. Network operators must fix these problems to keep users safe.
Tip: Users should update their devices and learn about new 5G security features. This helps lower risks during the switch.
Mixed Network Vulnerabilities
Using both 4G and 5G at the same time brings more risks. Devices often switch to 4G or even 3G when 5G is weak. This switch exposes users to old network problems. Attackers use the lack of mutual authentication in 4G. They catch identifiers like IMSI and can listen in or get in without permission.
Mixing 4G and 5G makes security harder. Attackers find differences and use them to attack. More IoT devices connect to 5G but still support 4G. These devices often have weak security, so threats spread easily. It gets harder to manage security when devices switch networks.
A comparison of risks in mixed network environments:
Aspect | 4G Only | 5G Only | Mixed 4G/5G Connectivity |
|---|---|---|---|
Vulnerabilities | Known flaws | Improved protection | Legacy flaws persist |
Security Risks | High | Lower | Increased attack surface |
Threats | IMSI-catcher, DDoS | AI-driven, edge risks | Downgrade, protocol exploits |
Breaches | More frequent | Less frequent | Higher risk during transition |
Switching to 5G gives better security, but using both networks keeps some risks. Users and operators need to stay alert to stop attacks and keep data safe.
User Tips
Choosing Secure Devices
Picking a secure device helps keep your data safe. It also protects your privacy. You should look for devices that meet global standards like 3GPP. These devices work with both 4g and 5g networks. Security is just as important as speed or looks. Here are some things to think about:
Devices need strong identity management. This lets the network check who you are.
Look for resource isolation. This keeps network parts apart and stops some attacks.
Devices should use asymmetric key encryption. This keeps your chats private, especially on 5g.
Pick devices that have secure registration and authentication. This stops fake users from getting in.
Devices should let you set up private networks. This keeps important data away from threats.
Keep your SIM card safe. SIM cards help with encryption and keys for 4g and 5g.
Think about what apps you use. Banking apps need more security than web browsing.
Tip: Devices with lightweight cryptography and multipath routing can handle 5g problems like eavesdropping or jamming better.
Best Practices
You can do things to keep your 4g and 5g devices safe. Experts say to use a zero-trust approach. This means the network checks every user and device each time. Here are some best ways to stay safe:
Check your device before you use it. Follow the maker’s rules for setup and updates.
Ask for regular security updates from your vendor. Updates fix new problems.
Use strong access controls. Only let trusted people and devices connect.
Watch network traffic for strange things. Finding problems early can stop attacks.
Use tools to find rogue devices. This is important with lots of IoT devices on 5g.
Check risks for each device and app. Some need more safety than others.
Plan for security from the start. Do not wait until later to add it.
Note: Even if your messages are encrypted, they can still be at risk from traffic analysis. Use full security plans for the best safety.
4G and 5G networks both have good and bad points for security. 5G uses better encryption and has a flexible setup. But, because 5G uses more software, it can have new problems. Experts say 5G is not always safer than 4G yet. 5G has issues like network slicing and tricky signaling. Both networks still have some weak spots:
Vulnerability | 4G Impact | 5G Impact |
|---|---|---|
High risk | Still possible | |
Signaling Protocols | Legacy flaws | New API risks |
Core Tunneling (GTP) | Data hijacking possible | Inherited in NSA |
People should pick devices that get updates often and use safety steps, like strong passwords and turning on security settings. Learning about risks and being careful helps keep your data safe on both 4G and 5G phones.
FAQ
Are 5G phones more secure than 4G phones?
5G phones have stronger security than 4G phones. 5G uses better encryption to keep data safe. It also hides user identities better than 4G. 4G phones have more known weak spots. If you want the best safety, pick a 5G phone.
Can 4G phones protect user privacy as well as 5G phones?
4G phones do not keep your privacy as safe as 5G. 5G networks hide your information before sending it out. 4G sometimes sends real user identities without hiding them. This makes it easier for someone to track you on 4G.
Do both 4G and 5G phones face cyber threats?
Both 4G and 5G phones can face cyber threats. 5G phones have new ways to protect users, but attackers still try to find weak spots. 4G phones are at more risk from old attack tricks. You should always be careful on both networks.
Will my phone switch between 4G and 5G networks?
Most new phones can switch between 4G and 5G networks. This helps keep your connection strong. But switching can let old 4G problems happen. To stay safer, keep your phone updated with the latest security.