
Network security matters a lot in 2025. There are new threats that change quickly. Attackers use AI and deepfakes now. They also attack through cloud and IoT devices. One weak spot can hurt your business. Look at these numbers:
|
Statistic Description |
Data / Value |
Year / Source |
|---|---|---|
|
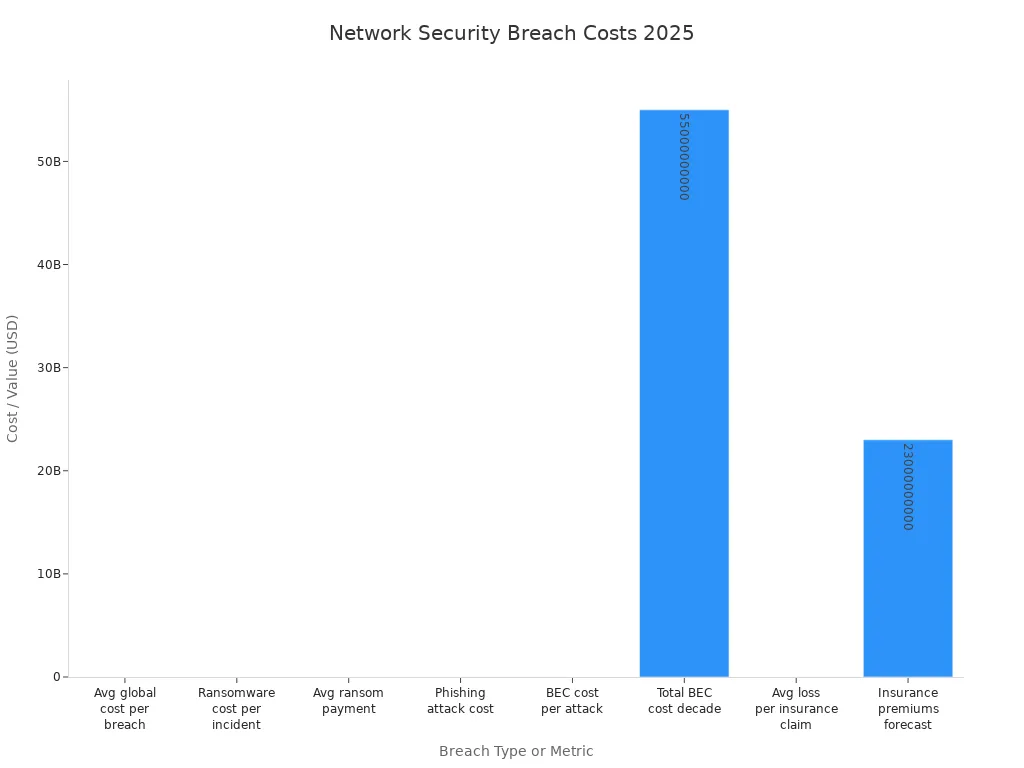
$4.88 million (10% year-on-year increase) |
2025, Viking Cloud citing IBM |
|
|
Ransomware average cost per incident |
$1.85 million (13% increase over 5 years) |
2025, Viking Cloud |
|
Average ransom payment |
$2 million (500% increase over 1 year) |
2025, Viking Cloud |
|
Phishing attack cost per incident |
$4.88 million |
2025, Viking Cloud |
|
Business Email Compromise (BEC) cost per attack |
$4.67 million (8.5% of breaches) |
2025, Viking Cloud |
Do not wait for a breach to check your network security. Look at your network security steps now. Use vulnerability scans and check your controls. Train your team well. A good network security plan keeps you safe from big risks, expensive attacks, and new threats.
Key Takeaways
-
Use the Zero Trust approach to check every user and device first. This stops attackers from moving around easily. It helps protect every part of your network.
-
Turn on multi-factor authentication to add more steps when logging in. This makes it much harder for attackers to use stolen passwords. It lowers security risks.
-
Update all software and devices often to fix security holes. This stops attackers from using known weaknesses.
-
Split your network into smaller parts to stop threats from spreading. Protect important data with stronger security controls.
-
Teach your employees about security topics like phishing and password safety often. Most breaches happen because people make mistakes.
1. Zero Trust Approach

What Is Zero Trust
Zero Trust is a way to keep your network safe. You do not trust anyone or anything right away. You must check every user, device, and connection before letting them in. You do not just guard the edge of your network. You protect all parts, like cloud, remote devices, and endpoints. This plan uses strong identity checks, multi-factor authentication, and encryption to keep your data safe.
Some people think Zero Trust is only for big companies or is too hard to use. That is not true. Small businesses also face cyber threats and can use Zero Trust without spending a lot. Some believe Zero Trust makes work slow, but it can make secure access easier with smart authentication. Zero Trust is not just about network connections. It also covers endpoint security and lets you see all devices.
Zero Trust works because it stops attackers from moving around your network. Micro-segmentation keeps threats in one place. Least privilege access means users only get what they need. Real-time monitoring and analytics find problems fast. You get better protection, lower costs, and easier compliance.
Implementation Steps
You can start with Zero Trust by doing these steps:
-
Assess your network: Find out where your sensitive data is. Check who can get to it and how they connect.
-
Set up strict identity verification: Use multi-factor authentication and biometric checks for all users.
-
Segment your network: Break your network into smaller parts. Use micro-segmentation to limit damage if a breach happens.
-
Apply least privilege access: Give users only the permissions they need. Review access often.
-
Monitor everything in real time: Use advanced network security tools to watch for strange behavior. Set up alerts for threats.
-
Encrypt data everywhere: Use encryption for data at rest and in transit. This keeps information safe from prying eyes.
-
Plan for hybrid environments: Make sure your network security strategies work for cloud, on-premises, and remote setups.
-
Train your team: Teach everyone about Zero Trust and why it matters for cyber protection.
You might have problems like old systems, not enough resources, and trouble seeing all your data. Go slow. Upgrade step by step. Talk with your staff. Use dashboards and analytics to manage security across your network. Zero-trust network access helps you stay ahead of threats and keeps your business safe.
2. Multi-Factor Authentication
Why Use MFA
You want to keep your network safe. Multi-factor authentication (MFA) helps you do that. It adds extra steps when you log in. You do not just use a password. You also use something you have, like your phone, or something you are, like your fingerprint. This makes it much harder for attackers to break into your network.
Most cyber attacks start with stolen passwords. Over 80% of security incidents happen because someone gets a password. If you use MFA, you stop most of these attacks. The average cost of a data breach is now $4.45 million. That is a huge risk for your business. Ransomware costs have also jumped by 500% in just one year. Without MFA, your network faces big financial losses, fines, and even legal trouble. You also risk losing your cyber insurance if you do not set up proper security.
Tip: MFA is one of the easiest ways to boost your network security. It protects your data, your money, and your reputation.
Setup Tips
You have many ways to set up MFA for your network. The best business solutions use a mix of methods:
-
Time-based one-time passwords (TOTP) from apps or SMS
-
Hardware security keys, like FIDO2 tokens
-
Biometric checks, such as fingerprint or face scans
Many companies use adaptive MFA. This means your network security changes based on risk. For example, you might need extra steps if you log in from a new place. Popular tools like Microsoft Authenticator, Windows Hello, and FIDO2 keys work well with cloud and on-premises networks.
When you set up MFA, keep it simple for your team. Choose methods that fit your network and your users. Test everything before you roll it out. Train your staff so they know what to expect. Good MFA makes your network security strong without slowing down your work.
3. Regular Updates and Patching
You must keep your network safe by updating often. Attackers move quickly and look for weak spots every day. If you do not update, you make it easy for them to get in.
Update Policy
Your business needs a clear update plan. This plan tells everyone when and how to update software and devices. Here are some important reasons to have a strong update plan:
-
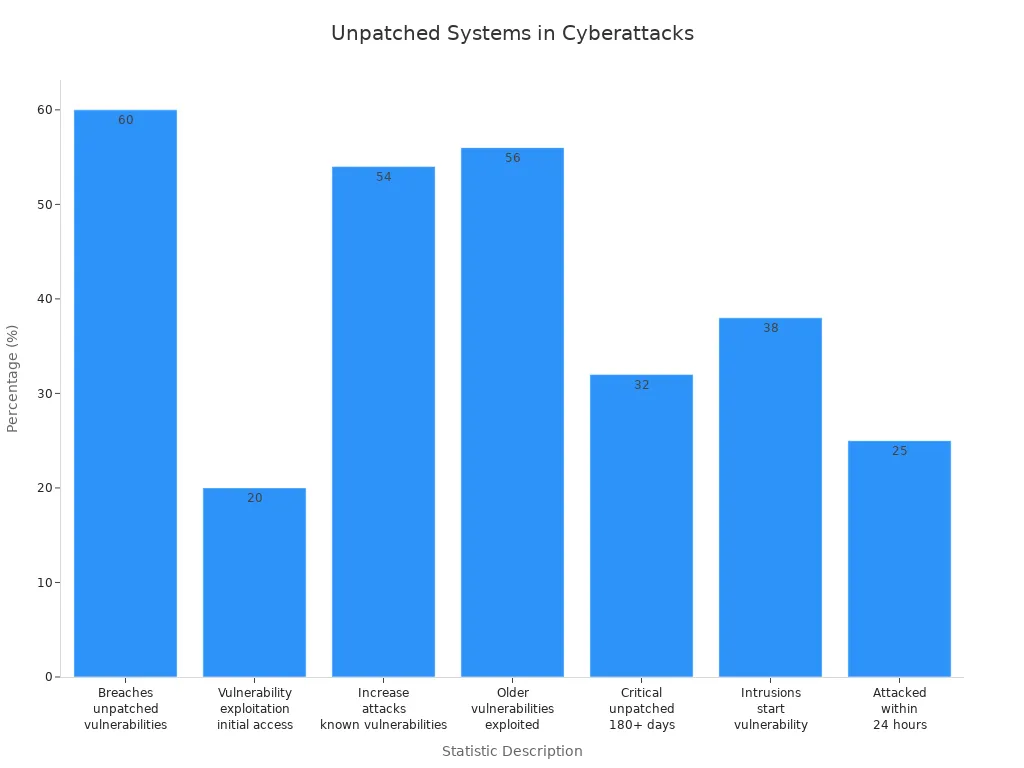
Software that is not patched is risky. More than 25% of weak spots get attacked in one day after people find out about them.
-
Reports say attacks on known weak spots went up by 54% in 2024.
-
The 2025 Verizon Data Breach Investigations Report says 20% of breaches happen because of weak spots. This is as common as stolen passwords.
Tip: Make a schedule for updates. Include all devices, firewalls, and software. Remember cloud apps and IoT devices too.
If you wait to update, you face big risks. Hackers can steal your data or put malware on your network. They can even shut down your network. The WannaCry attack and the Equifax breach happened because people missed patches. You do not want your business to be hurt like that.
Patch Management
Patch management helps keep your network strong. Here is a simple list to help you make a good patch plan:
-
Make a patch plan. This gives your team clear steps and roles.
-
Use tools to help patches install fast. This fixes problems quickly and stops mistakes.
-
Put important patches first. Use scores to find the biggest risks.
-
Test patches before you use them. Try them in a safe place to avoid trouble.
-
Keep a list of all your devices and software.
-
Have a way to go back if a patch causes problems.
-
Limit who can get in during patching. Use firewalls and least privilege rules.
-
Check and track patch status. Make sure every device gets the right updates.
-
Teach your team why updates matter for network security.
If you use special systems, you may not patch everything right away. In these cases, use extra firewalls and network segmentation. Intrusion prevention systems can help lower your risk.
Note: Waiting to patch can cause security problems and downtime. It can also cost you money. It is better to stop problems before they start.
4. Network Segmentation

Segmentation Benefits
Network segmentation helps keep your network safe. It splits your network into smaller parts. This makes it hard for attackers to move around. If someone gets into one part, they cannot reach the others. This keeps damage small and your business working.
Here are some main benefits of network segmentation:
-
Attackers cannot move easily because you keep areas separate. This stops threats from spreading.
-
You can use stronger security for important data. Each part has its own protection rules.
-
Segmentation helps you follow rules like PCI and HIPAA. You keep important data in safe places and make checks easier.
-
If a breach happens, it stays in one part. This helps you fix problems and recover faster.
-
Keeping important systems apart lowers your risk and makes attacks harder.
Tip: Segmentation also makes your network work better. You get less slowdowns and fix problems faster. It also helps with malware protection and encryption.
A study showed that Zero Trust Network Access helped companies a lot. They had 46% fewer access problems and 63% fewer hidden threats. They fixed issues 67% faster. These results show how segmentation helps security.
How to Segment
You do not need a lot of money to start segmentation. Follow these steps to make your network safer:
-
Set your goals. Think about what you want your network to be.
-
Check your network now. See where you have segments and where you need more.
-
Know your business needs. Decide which systems need the most protection.
-
Start with one area. Learn and improve as you go.
-
Write down your plan. Use diagrams to show VLANs, zones, and data paths.
-
Limit outside access. Make special portals for vendors.
-
Use firewalls to control traffic between parts.
-
Watch and check your network. Find risks early and stay safe.
-
Group similar things together. Do not make too many segments or it gets hard to manage.
Note: Use encryption for important parts. Keep patching and use malware protection. Good staff and leaders help you succeed.
5. Employee Security Training
Your team is very important for network safety. Even with good tools, people make mistakes. Most network problems happen because someone messes up. If you want strong security, you must teach your workers well.
Training Topics
You should teach many things in your training. Many problems start when someone clicks a bad link or shares a password. Recent reports show:
-
The Verizon Business Data Breach Investigations Report says 60% of breaches happen because of people, like mistakes or tricks.
-
Mimecast’s State of Human Risk Report found that 95% of data breaches are caused by human error.
-
Many workers think they can spot phishing, but almost half say they have been tricked.
To help your team, focus on these network security topics:
|
Training Topic |
Description |
|---|---|
|
Online Security Training |
How to keep personal and company data safe, spot threats, and protect the network. |
|
Authentication Best Practices |
Using strong passwords and multi-factor authentication for network access. |
|
Phishing and Email Security |
How to spot fake emails and tricks. |
|
Data Security and Privacy |
Keeping important network data safe and following privacy rules. |
|
Mobile and Remote Access |
Safe use of phones and secure network connections outside the office. |
|
Spotting fake content and learning about new network threats. |
You can also add special topics for different jobs, like safe coding for developers or cloud security for IT teams. This makes your training better.
Awareness Programs
You need programs that happen often, not just once. Regular network security lessons keep your team ready. One small accounting firm saw phishing clicks drop from 25% to less than 5% after three months of training. That’s a 73% improvement!
Here are some ways to make your network security programs work:
-
Run monthly phishing tests and network threat drills.
-
Use learning that changes based on each person’s weak spots.
-
Tell workers to report strange network activity. Reporting is the best way to see if your program works. Try to get over 70%.
-
Track progress with tests before and after training, incident reports, and worker feedback.
Tip: Make reporting easy. If your team reports network threats fast, you stay safer.
When you keep network security training fun and new, you build a team that protects your business. Your network stays safe, and you avoid big mistakes.
6. Network Security Monitoring
You need to watch your network all the time to keep it safe. Checking once is not enough. Continuous network security monitoring helps you find problems early. You can stop them before they get worse. When you monitor your network, you see what is happening right now. This lets you catch cyber attacks and mistakes fast.
Monitoring Tools
There are many network security tools for monitoring. Some of the best in 2025 are:
-
Exabeam Solutions: This tool uses smart tech to spot big threats. It helps you look into problems and act fast. Many businesses, like banks and hospitals, use it.
-
PRTG Network Monitor by Paessler: This tool checks your network and devices. It also watches IoT systems. You get alerts, maps, and dashboards to see what is happening.
-
Key things to look for:
-
Can the tool grow with your network?
-
Does it work with your other systems?
-
Is it easy for your team to use?
-
Does the price fit your budget?
-
Tip: Automation in continuous monitoring saves time and money. It helps you find and fix problems faster.
Threat Detection
Real-time threat detection is like having a guard for your network. It watches for strange things, like someone trying to break in. AI-powered systems can spot new cyber attacks. They find things that old tools might miss. These systems look for ransomware, phishing, malware, and insider threats. They can also block bad actions right away.
Here are some common threats you can catch with network monitoring:
-
Phishing attacks, including fake emails
-
Unpatched software and misconfigured devices
-
DDoS attacks and supply chain threats
-
Insider threats and business email compromise
When you use an intrusion detection system, you get alerts about strange activity. This helps you act fast and keep your network safe. Studies show that companies using security AI and automation find breaches 70% faster. They also save over $1.7 million on average. You get better prevention, stronger security, and peace of mind.
7. Incident Response Plan
When you think about network security, you need a strong incident response plan. This plan helps you act fast when a breach happens. You can stop threats, protect your network, and lower the risk of big losses from data breaches. Many businesses forget this step, but it is one of the most important parts of network security.
Plan Essentials
A good incident response plan keeps your network safe and ready for anything. Here are the essentials you should include:
-
Set up clear communication channels. List contact info for your team, outside experts, and anyone who needs to know about a breach.
-
Write down who does what. Assign roles for IT, management, legal, PR, and even your cyber insurance contacts.
-
Use both automated alerts and manual checks to spot problems. Make sure you can detect issues across your whole network.
-
Plan steps for containment, eradication, and recovery. You want to stop the threat, remove it, and get your network back to normal.
-
Hold lessons learned meetings after every incident. Use what you learn to make your network security even stronger.
-
Keep your plan simple and flexible. You want everyone to understand it, even during a stressful breach.
Tip: Involve people from all parts of your business, not just IT. This makes your plan stronger and helps you spot risks you might miss.
Many companies make mistakes like not updating their plan, not testing it, or leaving out key roles. Some write plans that are too general or too detailed. You want a plan that is just right—clear, direct, and easy to use.
Testing the Plan
Testing your incident response plan is just as important as writing it. If you do not test, you will not know if your network security works when it matters most. Regular tabletop exercises and drills help you find gaps and fix them before a real breach.
Studies show that companies with tested plans recover from data breaches much faster. IBM found that businesses with regular testing resolved incidents 54 days quicker and saved $1.49 million on average. You can cut the time it takes to spot and contain a breach from over 300 days to under 200 days. That means less downtime, fewer losses, and better protection for your network.
Here is a simple way to test your plan:
-
Run tabletop exercises with your team. Walk through a fake network breach and see how everyone responds.
-
Update your plan after each test. Fix any problems you find.
-
Review your plan every year or after any big changes in your network.
-
Make sure your contact lists and roles stay current.
Note: The faster you act, the less damage a breach can do. Some attacks, like ransomware, need a response in just a few hours to avoid major risk.
By testing and updating your plan, you keep your network security strong and ready for anything. You protect your business from the growing risks of data breaches and keep your operations running smoothly.
You can keep your business strong by following network security best practices. When you act early, you save money, protect your data, and build trust. Here’s a quick checklist to help you stay ahead:
-
Keep all devices and software updated.
-
Train your team on security threats.
-
Use strong firewalls and antivirus tools.
-
Back up your data often.
-
Watch your network for strange activity.
|
Benefit |
Why It Matters |
|---|---|
|
Stops leaks and keeps your business safe |
|
|
Keeps clients’ trust |
Shows you care about their information |
|
Meets regulations |
Avoids fines and legal trouble |
Keep reviewing your network security strategies. Stay alert and ready to adapt as threats change.
FAQ
What is the easiest way to start improving my network security?
Start by updating your software and devices. Turn on multi-factor authentication for every account. Teach your team about common threats. These steps help you protect your network fast.
How often should I update my network security plan?
Check your plan once a year. Update it after big changes in your business or technology. Regular reviews help you stay safe from new threats.
Do small businesses really need advanced security tools?
Yes, they do. Attackers go after all kinds of businesses. Simple tools like firewalls, antivirus, and monitoring software help keep your data safe.
What should I do if I suspect a cyber attack?
Act quickly. Unplug any device that might be attacked. Call your IT team or security provider. Follow your incident response plan. Fast action can stop more damage.
Can employee mistakes cause security problems?
Yes, they can. Most breaches happen when someone clicks a bad link or shares a password. Training helps your team spot threats and avoid mistakes.







