
You have more dangers now when you use your smartphone. In 2024, there were 2.8 million attacks each month from malware and unwanted software. The most secure mobile phone can help you stay safe from these problems. Here are the top 10 most secure mobile phones for private communication in 2025:
-
Apple iPhone 15 Pro Max
-
Samsung Galaxy S24 Ultra
-
Blackphone PRIVY 2.0
-
Bittium Tough Mobile 2C
-
Purism Librem 5
-
Sirin Labs Finney U1
-
K-iPhone by KryptAll
-
Connecta Mobile Encrypted Device
-
Hyperion Encrypted Phone
-
Silent Circle Blackphone BP1
These secure mobile phones use strong encryption, hardware security, and privacy tools. You need the best encrypted phones to keep your personal and work data safe. Pick a secure mobile phone to protect your privacy and have safe communication.
Key Takeaways
-
Mobile phones have more dangers now, like phishing and malware. Old software can also be risky. This makes security very important today.
-
Picking a secure phone helps keep your data safe. Look for strong encryption and hardware protection. Make sure the phone gets regular updates.
-
The best secure phones have special features. They use biometric locks and hardware kill switches. They also have encrypted messaging. These help stop hackers and spying.
-
Always update your phone and apps fast. Only use trusted app stores. Turn on multi-factor authentication to make your security stronger.
-
Choose a phone that matches what you need. Some people want privacy every day. Others need phones for tough places, cryptocurrency, or business data safety.
Why Pick the Most Secure Mobile Phones
New Dangers to Mobile Privacy
Phones are less safe now than before. Hackers use new ways to get your private info. Here are some big dangers you should know:
-
Mobile phishing, called mishing, tricks you with fake texts. Smishing is now most of mishing and grew by 22% last year.
-
Video phishing, or vishing, went up by 28%. Hackers use fake calls or videos to fool you.
-
AI-powered phishing uses fake PDF files to steal your data.
-
Many apps have third-party SDKs that can hide bad code. Over 60% of Android and iOS SDKs have these risks.
-
Sideloading apps from outside stores is not safe. About 23.5% of work phones have sideloaded apps, which may have malware.
-
Half of all phones use old operating systems. These phones are easy for hackers to attack.
Tip: Always update your phone and apps. Do not get apps from places you do not know. Use strong passwords and turn on multi-factor authentication to keep your data safe.
Safe Communication in 2025
You need safe ways to talk and text to keep things private. In 2025, hackers use smarter tools and new tech to break into phones. Safe communication uses strong encryption, like AES-256, to protect your data when you send it and when it is saved. Phones use SSL/TLS for network safety and certificate pinning to block fake servers from stealing your info.
|
Reason for Choosing |
Proof & Explanation |
|---|---|
|
Big Jump in Mobile App Dangers |
Mobile app attacks went up by 80% last year. Three out of four apps have security issues. Data breaches grew by 54%. |
|
Following Tougher Data Rules |
New rules like GDPR and CCPA need better security. Breaking these rules can cost a lot of money. |
|
More Risks from Mobile Threats |
Phishing, malware, and old software put your data in danger. Many apps do not have good security. |
|
Need to Keep Data Safe and Trust |
Companies must keep your data safe to keep your trust. Data leaks can hurt their name. |
|
Changing Security Plans |
Phones now use strong security, like safe places for banking apps and real-time updates. |
You should pick the most secure mobile phones to keep your life and work private. These phones use strong security and smart tools to keep your info safe. Safe communication helps you stay away from hackers and keeps your data private.
Best Encrypted Phones of 2025
Apple iPhone 15 Pro Max
The iPhone 15 Pro Max is one of the best encrypted phones. Apple uses iOS, which many experts say is the most secure mobile operating system. The phone has a secure enclave and a T2 security chip. It also has encrypted storage and Face ID. iOS 17 brings new anti-tracking for each app. It gives better permissions and Lockdown Mode to stop cyberattacks. Communication Safety protects your messages, AirDrop, FaceTime, and some third-party apps. Sensitive Content Warning lets you blur private photos and videos before you see them. Lockdown Mode gives extra protection from advanced threats.
Pros:
-
Strong encrypted communication across all Apple services.
-
Lockdown Mode for high-risk users.
-
Regular security updates.
-
Hardware and software work together for privacy.
Cons:
-
Only uses eSIM, which may not work everywhere.
-
Some hardware design choices can affect how you use the phone.
-
Law enforcement sometimes cannot access data, which can cause issues in some countries.
Best Use Case:
Pick this secure smartphone if you want easy privacy and strong encrypted features for daily life and work.
Samsung Galaxy S24 Ultra
The Samsung Galaxy S24 Ultra is one of the best phones for cybersecurity. It uses advanced security features to keep your data safe. Samsung Knox protects your device from the chip to the app layer. The phone has Lost Device Protection, App Protection, and Secure Wi-Fi. You get daily scans for malware and secure updates. Auto Block stops bad apps and suspicious connections.
|
Security Technology |
Description |
|---|---|
|
Lost Device Protection |
Tracks lost or stolen phones, even offline. |
|
App Protection |
Scans apps for malware during and after installation. |
|
Update Security Engine |
Keeps virus definitions current for better protection. |
|
Secure Wi-Fi |
Encrypts your data on public networks, great for banking or shopping. |
|
Auto Block |
Blocks apps from unknown sources and stops suspicious connections. |
Pros:
-
Multi-layered encrypted protection.
-
Frequent security updates.
-
Secure Wi-Fi for safe browsing.
Cons:
-
Some pre-installed apps may collect data.
-
Customization can be complex for new users.
Best Use Case:
Use this secure smartphone if you want a powerful device with advanced security for work and personal use.
Blackphone PRIVY 2.0
Blackphone PRIVY 2.0 is a privacy-focused mobile device with a hardened android system. It uses encrypted calling, messaging, and file sharing. The phone blocks tracking and lets you control app permissions. You get regular secure updates and a private app store.
Pros:
-
Hardened android OS for extra security.
-
Encrypted calls, texts, and files.
-
Private app store and frequent updates.
Cons:
-
Fewer apps available compared to standard Android phones.
-
May cost more than regular smartphones.
Best Use Case:
Pick this secure smartphone if you need private communication and want to avoid data leaks.
Bittium Tough Mobile 2C
Bittium Tough Mobile 2C is a secure smartphone made for tough places. It uses a hardware-based security platform with checks for firmware and hardware. The phone has tamper detection and a privacy mode. You get a secure boot process and a special switch for emergency data wiping. The strong build protects your phone from damage.
-
Secure boot and emergency wipe switch.
-
Military-grade build for harsh conditions.
Pros:
-
Multilayered encrypted security.
-
Strong protection against physical and software attacks.
-
Trusted manufacturing in Finland.
Cons:
-
Bulkier than regular phones.
-
Higher price due to advanced security features.
Best Use Case:
Use this secure smartphone if you work in risky jobs or need a phone that can survive tough conditions.
Purism Librem 5
Purism Librem 5 uses open-source software to give you control over your privacy. The phone runs PureOS, a Linux-based system. You and others can check the code for security problems. The phone has hardware kill switches for the camera, microphone, and radios. Purism shares hardware schematics and even x-rays of the device, so you know what is inside. The open-source way means the community can find and fix problems fast.
The Librem 5 uses privacy-by-design ideas and regular security updates. You get a secure smartphone that puts you in charge of your data.
Pros:
-
Open-source OS and hardware for full transparency.
-
Hardware kill switches for extra privacy.
Cons:
-
Fewer mainstream apps.
-
Not as polished as big brand phones.
Best Use Case:
Pick this secure smartphone if you want full control and transparency over your privacy.
Sirin Labs Finney U1
The Sirin Labs Finney U1 uses blockchain technology for security. It records transactions on a decentralized ledger, so hackers cannot change or steal your data. The phone uses decentralized authentication and advanced encryption. You get a built-in cold storage wallet for offline cryptocurrency storage. This keeps your digital assets safe from online threats.
-
Blockchain-based security for transactions.
-
Decentralized authentication and verification.
-
Cold storage wallet for offline crypto protection.
Pros:
-
Strong encrypted protection for digital assets.
-
Reduces risk of data breaches.
-
Good for cryptocurrency users.
Cons:
-
Focuses more on crypto than general use.
-
May not suit users who do not use blockchain.
Best Use Case:
Use this secure smartphone if you need to manage cryptocurrencies and want blockchain-level security.
K-iPhone by KryptAll
K-iPhone by KryptAll gives you encrypted voice calls using TLS and SRTP. The phone uses 256-bit AES encryption for VoIP calls. It changes the firmware to encrypt audio, so only the person you call can hear you. Calls go through a global network of encrypted servers in countries where interception is illegal. The phone skips public telephone switches and uses WiFi or cellular data for secure calls.
|
Security Feature |
Details |
|---|---|
|
Encryption starts at the device level, securing call audio |
|
|
Used for signaling and voice data encryption |
|
|
Global encrypted server infrastructure |
Servers in over ten countries with legal protections |
|
Internet-based transmission |
Calls use WiFi or cellular data, not public switches |
|
NIST and CSE certified AES hardware |
Hardware AES encryption validated by US and Canadian standards |
|
FIPS 140-2 validated cryptographic engine |
Meets US federal cryptographic standards |
Pros:
-
Multi-layered encrypted voice call protection.
-
Global server network for privacy.
-
Meets top international security standards.
Cons:
-
Expensive compared to regular phones.
-
Focuses mainly on voice call security.
Best Use Case:
Pick this secure smartphone if you need the highest level of encrypted voice communication.
Connecta Mobile Encrypted Device
Connecta Mobile Encrypted Device gives you 256-bit encryption for all stored data. Voice and data transmissions are encrypted to stop eavesdropping. The phone uses VPN services to hide your internet activity. Blockchain validation checks the software and hardware. You can manage the device remotely, lock or wipe it if lost, and only allow approved apps. The phone does not track your data or store call records.
-
256-bit encrypted storage and transmission.
-
VPN and blockchain validation.
-
Remote management and strict app control.
-
No data tracking policy.
Pros:
-
Strong encrypted protection for enterprise users.
-
Easy remote management.
-
No data tracking for privacy.
Cons:
-
Limited app choices.
-
May need IT support for setup.
Best Use Case:
Use this secure smartphone if you manage sensitive business data and need enterprise-level encrypted security.
Hyperion Encrypted Phone
Hyperion Encrypted Phone protects you from both physical and remote attacks. The phone uses hardware-level protection and limits app installations. It disables big tech apps and only allows trusted third-party apps. Security patches come quickly through a secure pipeline. All communications use end-to-end encryption and a VPN. You can turn off all radios, like WiFi, Bluetooth, NFC, and GPS, to stop data leaks. The phone finds and isolates malware right away. If someone tries to steal your phone, you can start a self-destruct protocol to wipe all data.
|
Security Feature |
Description and Protection Mechanism |
|---|---|
|
Hardware-level protection |
Protects user data at the hardware level, reducing app and software risks. |
|
App installation restrictions |
Only allows trusted apps, disables big tech apps. |
|
Secure patch deployment pipeline |
Delivers security patches quickly and securely. |
|
End-to-end encryption + VPN |
Encrypts all communications and metadata. |
|
Automatic data encryption |
Encrypts all stored data on the device. |
|
Internal radios disablement |
Lets you turn off all radios to prevent leaks. |
|
Malware identification and isolation |
Detects and isolates malware instantly. |
|
Self-destruct protocol |
Wipes device if compromised. |
Pros:
-
Full encrypted protection for data and communication.
-
Fast security updates.
-
Self-destruct feature for emergencies.
Cons:
-
May be harder to use for beginners.
-
Fewer app choices.
Best Use Case:
Use this secure smartphone if you need maximum protection against both digital and physical threats.
Silent Circle Blackphone BP1
Silent Circle Blackphone BP1 uses SilentOS, a hardened android system. The phone gives you anonymous search and privacy-enabled apps. It turns off Wi-Fi except for trusted hotspots. You get more control over app permissions than on most Android phones. The phone supports encrypted calling, texting, video chat, browsing, file sharing, and conference calls. You get frequent secure updates directly from Blackphone.
-
Built-in encrypted communication for calls, texts, and video.
-
Private cloud VPN for all data.
-
Frequent secure updates.
Pros:
-
Privacy-focused mobile device with encrypted communication.
-
Hardened android OS for extra security.
-
Frequent updates and strong app controls.
Cons:
-
Limited app ecosystem.
-
May not have all features of mainstream phones.
Best Use Case:
Pick this secure smartphone if you want a privacy-focused mobile device with encrypted communication and strong app controls.
What Makes the Best Secure Smartphones
Hardware Security
Strong hardware security is important for a secure smartphone. The best phones use sensors like fingerprint and Face ID. These help you unlock your phone in a safe way. Hardware secure storage, like Apple’s Secure Enclave or Google’s Titan M chip, keeps your data safe from hackers. Secure boot stops bad software from running when you turn on your phone. Some phones, like the Purism Librem 5, have switches to turn off the camera, microphone, and radios. These switches help you control your privacy. Tamper-resistant cases and trusted places in the phone add more safety. Hardware Security Modules (HSMs) keep important data safe and help with encrypted actions. Phones like the Bittium Tough Mobile 2C have military-grade encryption and use AES-256 for full disk protection.
Encryption Standards
The best secure smartphones use strong encryption to keep your info safe. Full disk encryption protects all your files and messages, even if your phone is stolen. Phones like the Blackphone PRIVY 2.0 and K-iPhone by KryptAll use end-to-end encrypted calls and texts. You also get encrypted storage and backups. These features keep your data safe from hackers. Military-grade encryption, like AES-256, is common in the safest phones.
Secure Operating Systems
A secure smartphone needs a safe operating system. iOS has a closed system with encrypted data and regular updates. Android lets you use custom ROMs and antivirus apps for extra safety. Secure systems use sandboxing to stop malware from spreading. You get encrypted backups and privacy tools like biometrics and passcodes. Phones like the Purism Librem 5 and Silent Circle Blackphone BP1 use open-source or special systems for better privacy.
Regular Updates
You need to keep your secure smartphone updated to stay safe. The best phones get security updates often. Apple iPhones and Samsung Galaxy S24 Ultra get monthly updates for at least five years. Google Pixel 8 series gives seven years of updates. Updates fix problems and add new security features. Here is a quick look at how long updates last:
|
Brand/Model |
Security Update Duration |
Update Frequency |
Notes |
|---|---|---|---|
|
Google Pixel 8 series |
7 years |
Monthly |
New benchmark with 7 years of security patches and upgrades; monthly patches arrive on time. |
|
Apple iPhones |
At least 6 years |
Monthly (implied) |
Exceeds stated 5-year commitment; consistent long-term support across models. |
|
Samsung (recent) |
5 years (some models 3) |
Monthly to variable |
Recent phones get 5 years; older models get 3 years; Galaxy S24 series up to 7 years. |
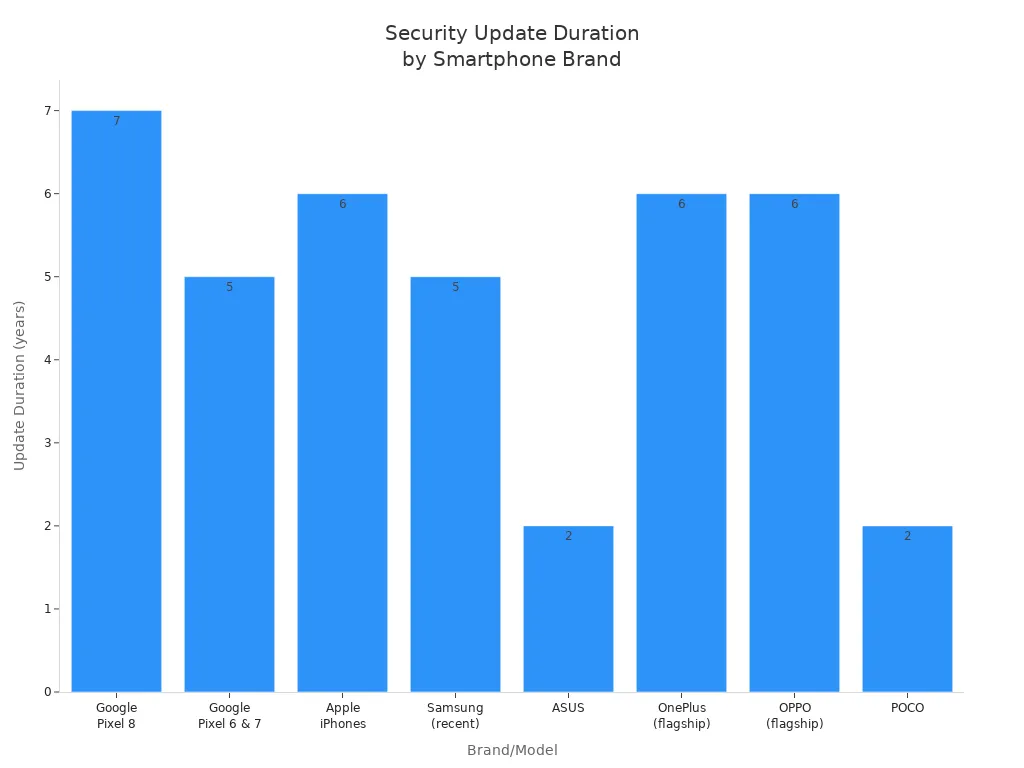
Tip: Always check for updates and install them fast. This keeps your data and privacy tools strong.
Pros, Cons, and Use Cases
Strengths of Each Model
Secure phones have many good features. The top 10 secure phones share some strong points. These features help keep your data safe and your chats private.
|
Common Strengths in Top 10 Secure Mobile Phones |
Description |
|---|---|
|
Open-Source Software |
You can look at the code and fix problems fast. |
|
Hardware Kill Switches |
You can turn off the camera and mic with a switch. |
|
Military-Grade Encryption |
Strong encryption keeps your calls and data safe. |
|
Secure Communication Platforms |
Calls and texts use end-to-end encryption. |
|
Privacy-Focused Operating Systems |
Special systems help block hackers. |
|
Regular Security Updates |
You get patches to fix security holes. |
|
Biometric Authentication |
Unlock your phone with your face or fingerprint. |
|
Full Disk Encryption |
All your stored data is protected from thieves. |
|
Secure Booting |
Your phone checks for bad software when starting. |
|
Sandboxing of Apps |
Apps stay separate so malware cannot spread. |
|
Secure App Ecosystem |
Safe app stores lower the risk of malware. |
|
Device Management Features |
You can find, lock, or wipe your phone if lost. |
|
Physical Security Measures |
The phone has a strong build and hardware protection. |
Note: These features work together to keep your phone and information safe.
Potential Drawbacks
Even the best secure phones have some problems. You might see these common issues:
|
Aspect |
iOS (Highly Secure Phones) |
Android (Flexible but Potentially Less Secure) |
|---|---|---|
|
Ecosystem |
Closed system means fewer choices and apps. |
Open system has more apps but can be less safe. |
|
Device Variety |
Not many models and they cost more. |
More models but not all are secure. |
|
Updates |
Most devices get updates often. |
Some phones get updates late or not at all. |
|
Security Risks |
Lower risk but you have less control. |
More control but higher risk if you are not careful. |
|
Cost |
Usually costs more money. |
Can be cheaper but may not have strong security. |
|
User Control |
Less customization to keep you safe. |
More options but this can weaken security. |
You may have to give up some choices or pay more for better security.
Who Should Choose Which Phone
Pick a secure phone that fits your needs:
-
If you want easy updates and strong privacy, pick iPhone 15 Pro Max or Samsung Galaxy S24 Ultra.
-
If you want full control and open-source tools, try Purism Librem 5.
-
If you work in tough places or need strong protection, Bittium Tough Mobile 2C is a good choice.
-
If you use cryptocurrency, Sirin Labs Finney U1 gives you blockchain security.
-
If you want the best voice call privacy, K-iPhone by KryptAll is best.
-
If you manage business data, Connecta Mobile Encrypted Device or Hyperion Encrypted Phone will help keep you safe.
Tip: Think about what you do every day and what you need most from your phone. The right phone will help you feel safe and protected.
Key Features of the Most Secure Mobile Phone

End-to-End Encryption
The most secure mobile phone keeps your calls, texts, and files safe. It uses end-to-end encryption. This means your messages get scrambled on your phone before they go anywhere. Only you and the person you talk to can read them. Hackers and phone companies cannot see your messages. Messaging apps like Signal use special rules to keep your chats private. You are safe from people trying to listen in or steal your texts and calls. Your secret keys stay on your phone, so it is hard for hackers to take them. Some phones let you check codes or scan QR codes to make sure your chat is safe. Even when your messages are saved, they stay protected with full disk encryption. But you should know that if someone gets into your phone, they might still get your data.
-
Your device scrambles messages before sending.
-
Only you and your friend can read them.
-
Secret keys never leave your phone.
-
Stops others from listening or reading your messages.
-
You can check codes to make sure your chat is safe.
Tip: Use encrypted messaging apps and update your phone often for the best privacy.
Biometric Security
Biometric security lets you unlock your phone with your fingerprint or face. These are special to you and hard to copy. This makes your phone safer from other people. Most secure phones now use this kind of lock. You do not have to remember a password or carry a card. Some phones check if you are really there, not just a picture. Only you can open your phone with your fingerprint or face. This way is very accurate and works almost every time. It is easy to use and keeps your phone private. But you should still keep your fingerprint or face data safe, because you cannot change them if stolen.
-
Fingerprint and face unlock are quick and safe.
-
Only you can open your phone.
-
New systems stop fake unlocks.
-
Biometric locks are now common in secure phones.
Hardware Kill Switches
Some secure phones have hardware kill switches. You can flip a switch to turn off the camera, mic, or radios. This stops apps or hackers from spying on you. When you use the switch, your phone cannot listen or watch. Kill switches help you control your privacy. You can use them in meetings or when you travel. This is good for people who want to block spying fast.
-
Flip a switch to turn off camera, mic, or radios.
-
Stops spying and tracking right away.
-
Use kill switches for more privacy when needed.
Privacy-Focused Apps
The most secure phones have special apps for privacy. These apps help you send safe messages, make private calls, and browse without being tracked. They do not collect your data or show ads. You can get safe apps for email, files, and video calls. The app store only has trusted apps, so you do not get malware. You get updates often to keep your apps safe.
|
Privacy App Type |
What It Does |
|---|---|
|
Encrypted Messaging |
Keeps your chats private |
|
Encrypted Phone Calls |
Protects your voice conversations |
|
Secure Browsing |
Blocks trackers and ads |
|
Secure Applications |
Safeguards your files and emails |
Note: Pick apps from the secure app store to keep your data safe and your privacy strong.
How We Selected the Best Encrypted Phones
Selection Criteria
You want a phone that keeps your private life safe. We made a list of rules to help you pick. Here is how you can tell if a phone is really secure:
-
End-to-End Encryption: Your phone should use end-to-end encryption. Only you and the person you talk to can read messages or hear calls.
-
Strong Encryption Algorithms: Look for phones with strong encryption like AES 256-bit or RSA 2048-bit. These codes are very hard for hackers to break.
-
Secure Operating System: Pick a phone with a special operating system made for privacy. Do not choose phones with normal systems that lack extra protection.
-
Remote Wiping and Data Destruction: Choose a phone that lets you erase all your data if you lose it. This keeps your information safe from strangers.
-
Network Security Features: Check for things like secure VPN, WiFi encryption, and tools that find network attacks. These keep your phone safe when you go online.
-
Trusted Provider Reputation: Always look at the company’s history. A good record means fewer hidden dangers.
Tip: If a phone has all these things, you can trust it to keep your secrets safe.
Research and Testing
You need to know your phone’s security is real, not just a promise. We tested each phone with trusted tools and methods. These tools look for weak spots in the phone’s code, apps, and network. Here is a table with some of the main tools we used:
|
Tool Name |
Testing Methods Used |
Key Features |
Pros |
Cons |
|---|---|---|---|---|
|
Fortify on Demand |
Static and Dynamic Analysis |
Finds weak spots in code and data storage |
Detailed reports; works with many systems |
Can be pricey; setup may be complex |
|
HCL AppScan |
Vulnerability Scanning |
Checks code and server connections |
Advanced automation; deep testing |
Setup can be hard; high cost |
|
AppSweep |
Automated Security Testing |
Spots data leaks and unsafe network use |
Easy to use; works in the cloud |
Limited iOS support; some features cost more |
|
Veracode |
Static and Dynamic Analysis |
Looks for bad code and network problems |
Actionable reports; fits many workflows |
Expensive; setup can be tricky |
|
Synopsys |
Static, Dynamic, Interactive |
Finds risks in code and network communication |
Supports many platforms; clear suggestions |
Takes time to set up; higher price |
Each tool checks for different problems. Using more than one tool gives you a better idea of how safe a phone is. This helps you make a smart choice to protect your privacy.
Tips for Secure Communication
Everyday Security Practices
You can keep your phone safe by doing simple things each day. These habits help protect your private messages and calls.
-
Use a strong passcode, fingerprint, or face to lock your phone.
-
Update your phone and apps as soon as you see an update.
-
Use a VPN when you use public Wi-Fi. This keeps your data safe.
-
Only get apps from trusted stores like the App Store or Google Play. Always check what permissions an app wants.
-
Turn on two-factor authentication for your accounts. This adds extra safety.
-
Back up your data often. Use cloud services or an external drive.
-
Turn off Bluetooth when you do not need it. This lowers the chance of someone connecting to your phone without you knowing.
Tip: Set up remote wipe. If you lose your phone, you can erase your data from anywhere.
Avoiding Common Risks
There are many risks when you use your phone for secure communication. Hackers try to steal your information in easy ways. You can avoid most problems if you stay alert.
-
Do not skip updates. Updates fix security problems.
-
Only install apps from official stores. Unofficial apps may have malware.
-
Limit what apps can do. Give them only the access they need.
-
Turn off auto-connect to Wi-Fi. This stops your phone from joining unsafe networks.
-
Watch for strange activity. Set up alerts for anything suspicious.
-
Use strong and different passwords for every account.
-
Always turn on device lock features.
Note: Encrypted messaging apps help keep your chats private from others.
Recommended Security Tools
You can use special tools to make your phone even safer. These tools help you build a secure way to talk and text every day.
|
Tool Type |
What It Does |
Example Apps |
|---|---|---|
|
Encrypted Messaging |
Keeps your texts and calls private |
Signal, WhatsApp |
|
VPN |
Hides your internet activity on public Wi-Fi |
NordVPN, ProtonVPN |
|
Password Manager |
Stores strong and different passwords |
Bitwarden, 1Password |
|
Remote Wipe App |
Lets you erase your phone if lost or stolen |
Find My iPhone, Find My Device |
|
Security Scanner |
Checks your phone for threats |
Malwarebytes, Lookout |
Remember: Using these tools together gives you the best protection for your secure communication.
Picking the most secure mobile phone keeps your chats and data safe. The top 10 encrypted phones use strong encryption and hardware security. They also have special features to protect your privacy. You should update your phone often and use safe habits every day.
Always pay attention and put privacy first. Choose a phone that works for you and keeps your info safe.
FAQ
What makes a phone truly secure?
A secure phone keeps your data safe with strong encryption. It gets regular updates and has privacy tools. You can control what apps do and what data they use. Some phones have kill switches and locks that use your face or finger. These features help keep your phone safe. Always look for these things before you buy a phone.
Can you use regular apps on secure phones?
You can use some normal apps, but not every app. Secure phones limit which apps you can get to keep you safe. You should only get apps from trusted stores. Some secure phones have their own stores with safe apps.
How often should you update your secure phone?
Update your phone as soon as you see an update. Updates fix problems and add new safety tools. Regular updates help stop hackers. Try to set your phone to update by itself.
Do secure phones protect against all threats?
Secure phones block most online dangers. They use encryption and privacy tools to help you. No phone can stop every attack. You still need to use strong passwords and pick safe apps to stay safe.
Is it hard to switch to a secure phone?
Most people find it easy to switch to a secure phone. You might need to learn new settings or try new apps. Many secure phones have guides to help you. You can move your contacts and files with backup tools.




