
Are you trying to find the safest phone for work or home? Here are the top 10 high-security smartphones for 2025:
Google Pixel 9 Pro XL
Samsung Galaxy S25 Ultra
Apple iPhone 17 Pro Max
Purism Librem 5
Bittium Tough Mobile 2C
Vertu Metavertu 2
Samsung Galaxy A36 5G
Google Pixel 9a
OnePlus Nord 4
Apple iPhone 16 Pro Max
You want the best secure smartphones because threats are always growing. These secure phones have hardware kill switches and AES-256 encryption. They also have tamper-proof builds and privacy-focused choices. Each secure phone gives strong protection and regular updates. They have features like end-to-end encryption. Choose the most secure phone that matches your needs. You might want a secure phone for work, a privacy device, or the safest smartphone for everything.
Key Takeaways
High-security smartphones keep your private data safe from more cyber threats at work and home. – You should choose phones with strong encryption, secure boot, biometric authentication, and regular updates. – Business phones have many risks like ransomware, phishing, and insider threats that can cause big problems. – Privacy-focused phones with hardware kill switches and open-source software help you control your data. – Keep your phone safe by updating it often, using strong passwords, and staying away from untrusted apps and networks.
Why Choose a High-Security Smartphone
You use your phone for many things. You send emails and store photos. You also do work tasks on it. Have you thought about how much private data is on your phone? Cyber threats are growing fast. Attackers know your phone holds lots of important information. That is why choosing a high-security smartphone matters more now.
Business Security Risks
Phones used for work face big security risks. Hackers attack business smartphones in many ways. Here are the most common attacks in 2024 and 2025:
Cyberattack Type | Description and Relevance to Business Smartphones in 2024-2025 |
|---|---|
Ransomware | Stops your business, leaks data, and can lock your device. |
Vulnerabilities | Uses weak software to make your secure phone easy to attack. |
Defense Evasion | Gets past security tools and hides malware on your phone. |
Drive-by Compromise | Infects your device with fake ads or bad websites. |
Phishing Attacks | Tricks you with fake emails or texts to steal your data. |
Malware | Puts bad software on your phone to steal or ruin information. |
DDoS Attacks | Stops services you need and hurts your work. |
Supply Chain Attacks | Attacks apps or services you use and puts your phone at risk. |
Insider Threats | People with access may use your information in the wrong way. |
Business Email Compromise | Goes after your email on your secure phone to steal data. |
A breach is not just lost files. The damage can be much worse. Here is what can happen if a business has a data breach:
Impact Type | Description / Data |
|---|---|
Reputational Damage | 62% of companies say mobile breaches hurt their name, and 41% say the harm lasts a long time. |
Financial Loss | A breach in the U.S. costs about $3.86 million. |
Data Loss | Private data gets out and puts your business in danger. |
Downtime | Work stops while you fix the problem. |
Penalties and Fines | You could get in legal trouble and pay big fines. |
Additional Equipment Loss | Losing devices makes your costs go up. |
Insurance Costs | Your insurance costs more after a breach. |
Vulnerabilities | Phones are easy to trick and may not have strong protection. |
Employee Risk | Mistakes or lost phones can cause a breach. |
Cybercriminal Adaptation | Attackers keep finding new ways to break into your secure phone. |
You need a secure phone to keep your business safe. It also protects your clients and your good name. Good security is not just for big companies. All businesses face these risks.
Personal Privacy Threats
Your private life is also in danger. Many apps collect more data than you think. Some share your private data with other people or groups. Studies show that contact-tracing and social apps take your location, name, phone number, and more. Some apps ask for your camera, microphone, or messages for no clear reason.
Did you know? Many apps share your data with others and do not tell you who gets it or what they do with it. Some apps do not use good encryption, so your data is not safe.
Surveillance is everywhere now. You may think your phone is private, but it is often not. Many people worry about losing privacy and staying anonymous. A privacy-focused secure phone helps you control your information.
Cyber threats are not slowing down. Experts say AI-powered attacks will go up by 45% in 2025. Deepfake scams and zero-click malware are happening more. With more 5G and IoT devices, your secure phone faces more risks. SIM card swap scams and cloud data breaches are also rising. You need a high-security smartphone to keep your data safe and protect your privacy every day.
What Makes the Best Secure Smartphones

Key Security Features
When you want the best secure smartphones, you need to know what keeps them safe. A secure phone keeps your information security strong every day. Look for these features:
End-to-end encryption: This keeps your calls, texts, and files private. Only you and the person you talk to can see them.
Data encryption: Your secure phone mixes up your data. If someone steals your device, they cannot read it.
Secure boot: This checks your phone’s software each time you turn it on. It stops hackers from putting bad programs on your phone.
Malware protection: The best secure smartphones block viruses and spyware.
Two-factor authentication: You use a password and something else, like a code or fingerprint. This makes it much harder for someone to get in.
Biometric authentication: You can unlock your secure phone with your face or fingerprint.
Advanced authentication: Some phones use your voice or eyes for even more information security.
Privacy features: Hardware kill switches and privacy-focused operating systems help you control your data.
Secure communication protocols: These keep your messages and calls safe from spying.
Tip: Always use two-factor authentication and end-to-end encryption for the best data security.
Selection Criteria
You want a secure phone that works for you. Here is how we chose the top 10:
Criteria | Why It Matters for Information Security |
|---|---|
End-to-end encryption | Keeps your chats and calls private |
Two-factor authentication | Adds a strong layer of protection |
Regular security updates | Fixes new threats fast |
Advanced security features | Stops hackers and protects your information security |
Biometric security | Makes unlocking your phone safe and easy |
Privacy-focused OS | Gives you more control over your data |
Secure hardware design | Stops tampering and keeps your secure phone safe |
Price and value | Makes sure you get the best secure smartphones for your budget |
You should always look for these features before you buy a secure phone. This helps you get strong information security and feel safe.
Top 10 Most Secure Phones of 2025
Google Pixel 9 Pro XL
This phone keeps your data safe and updates quickly. The Google Pixel 9 Pro XL uses the Titan M3 security chip. This chip helps stop tampering and phishing. You get security updates as soon as Google sends them. The phone uses end-to-end encryption for calls and messages. It also has secure boot and strong malware protection. You can use this phone for work or home. It gives you strong security and privacy.
Key Features:
Titan M3 security chip
End-to-end encryption for calls and texts
Regular and fast security updates
Secure boot and malware protection
Best for: Business users, privacy-focused people, and anyone who wants the most secure phone with the newest Android features.
Samsung Galaxy S25 Ultra
The Samsung Galaxy S25 Ultra is powerful and secure. Samsung Knox protects your data at every step. You get a secure folder for private files and apps. The phone uses fingerprint and face unlock. Samsung gives you regular security updates. The S25 Ultra supports end-to-end encryption for Samsung Messages and calls. This phone is good for business or personal use.
Key Features:
Samsung Knox security platform
Secure Folder for private data
Biometric authentication (fingerprint, face)
Regular security updates
Best for: Business workers, Android fans, and anyone who wants a feature-rich, most secure phone.
Apple iPhone 17 Pro Max
Apple is known for privacy and security. The iPhone 17 Pro Max uses the Secure Enclave chip to keep your data safe. It has Face ID and Touch ID for easy and strong unlocking. Apple gives you end-to-end encryption for iMessage and FaceTime. You get regular iOS updates for the latest security. If you want a secure phone that is simple to use, this iPhone is a great pick.
Key Features:
Secure Enclave chip
Face ID and Touch ID
End-to-end encryption for iMessage and FaceTime
Fast and regular iOS security updates
Best for: Business users, privacy-focused people, and anyone who wants the most secure phone with iOS.
Purism Librem 5
The Purism Librem 5 is made for privacy. It runs PureOS, which is open-source GNU/Linux. You do not have to worry about hidden tracking from big tech. The phone has physical kill switches for cellular/Wi-Fi, Bluetooth, microphone, and camera. You can turn these off for real privacy. The cellular modem is separate from the main CPU and memory. This stops attackers from using the network to get your data. The Librem 5 uses both hardware and software privacy tools. You get full control over your data.
Best for: Privacy-focused users, tech fans, and anyone who wants the most secure phone with open-source software.
Bittium Tough Mobile 2C
This phone is tough and keeps secrets safe. The Bittium Tough Mobile 2C meets military standards for shock, vibration, temperature, and humidity. It uses a tamper-proof secure element. If someone tries to break in, it erases all data, even if the battery is dead. All data, including SD cards, is encrypted with AES-256. Secure boot checks hardware and software every time you start the phone. Only Bittium-signed firmware works. Dual-boot lets you run two operating systems. You can keep work and personal data apart. Secure containers and VPN tunnels keep your apps and data safe. Privacy Mode turns off microphones, cameras, and Bluetooth. The phone is made in Finland and is certified. Security updates come over-the-air. You can manage devices, wipe them remotely, and use quantum-safe VPN.
Note: The Bittium Tough Mobile 2C is certified for national security and NATO Restricted communications.
Best for: Government, military, business leaders, and anyone who needs the most secure phone for tough situations.
Vertu Metavertu 2
This phone gives you luxury and security together. The Vertu Metavertu 2 uses high-end materials and gives a secure mobile experience. It has a special security chip and supports encrypted calls and messages. You get a private app store and secure cloud storage. Vertu offers concierge services for extra privacy. If you want the most secure phone with a luxury feel, pick this one.
Key Features:
Dedicated security chip
Encrypted calls and messages
Private app store and secure cloud
Luxury design and materials
Best for: Executives, VIPs, and anyone who wants a luxury, most secure phone.
Samsung Galaxy A36 5G
You do not need to spend a lot for a secure phone. The Samsung Galaxy A36 5G gives you strong security at a good price. It uses Samsung Knox for device protection. You get fingerprint or face unlock and regular security updates. The phone supports secure folders for private files. If you want the most secure phone on a budget, this is a smart pick.
Key Features:
Samsung Knox security
Biometric authentication
Secure Folder for private data
Regular security updates
Best for: Budget users, students, and anyone who wants secure mobile phones without spending too much.
Google Pixel 9a
This phone stays secure for many years. The Google Pixel 9a gives you long-term support and fast updates. Google promises OS and security updates until at least March 2032. You get updates right away and new features through Pixel Drops.
Pixel Model | OS and Security Update Support Until |
|---|---|
Pixel 9a | At least March 2032 |
Pixel 9 series | At least August 2031 |
Pixel 9 Pro Fold | At least August 2031 |
Pixel 8a | At least May 2031 |
Pixel 8 series | At least October 2030 |
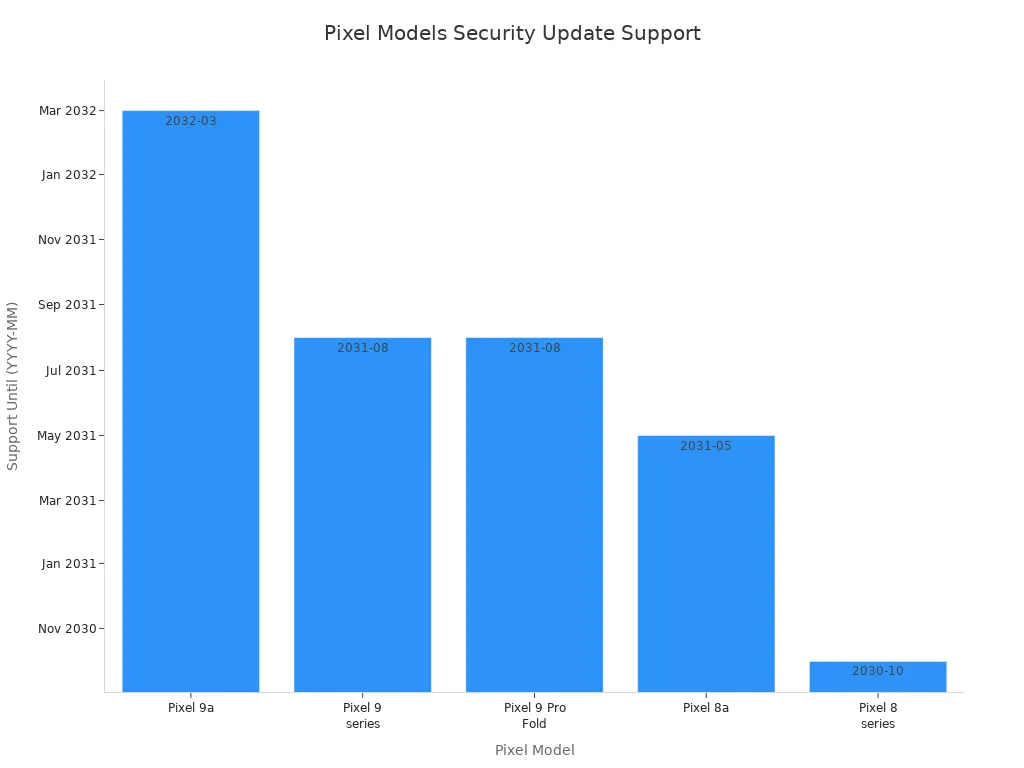
The Pixel 9a uses Google’s security chip and supports end-to-end encryption for calls and texts. This phone is easy to use and keeps your data safe for a long time.
Best for: Everyday users, families, and anyone who wants secure mobile phones with long-term support.
OnePlus Nord 4
This phone is secure, fast, and affordable. The OnePlus Nord 4 uses secure boot and gets regular security updates. You get fingerprint or face unlock and a privacy-focused mode for sensitive tasks. The phone supports encrypted calls and messages. If you want the most secure phone with great value, the Nord 4 is a good choice.
Key Features:
Secure boot and regular updates
Biometric authentication
Privacy-focused mode
Encrypted calls and messages
Best for: Young professionals, students, and anyone who wants the most secure phone at a mid-range price.
Apple iPhone 16 Pro Max
This phone is secure and trusted. The iPhone 16 Pro Max uses Apple’s Secure Enclave and supports Face ID and Touch ID. You get end-to-end encryption for iMessage and FaceTime. Apple gives you regular iOS updates to keep your phone safe. If you want the most secure phone with Apple’s system, this is a great pick.
Key Features:
Secure Enclave chip
Face ID and Touch ID
End-to-end encryption for iMessage and FaceTime
Fast and regular iOS security updates
Best for: iOS fans, business users, and anyone who wants the most secure phone with Apple’s ecosystem.
Secure Mobile Phones Comparison Table

Picking a secure phone can be hard. You want to see all the facts together. This table lets you compare the top secure phones for 2025. You can find the best secure phone for you in seconds.
Phone Model | Core Security Features | OS | Price Range | Best Use Case |
|---|---|---|---|---|
Google Pixel 9 Pro XL | Titan M3 chip, secure boot, fast updates | Android | $$ | Business, privacy, daily use |
Samsung Galaxy S25 Ultra | Samsung Knox, secure folder, biometrics | Android | $$ | Business, feature-rich use |
Apple iPhone 17 Pro Max | Secure Enclave, Face/Touch ID, iOS updates | iOS | $$ | Business, privacy, iOS fans |
Purism Librem 5 | Hardware kill switches, PureOS, open-source | PureOS | $ | Privacy, tech fans |
Bittium Tough Mobile 2C | Tamper-proof, dual-boot, quantum-safe VPN | Android | $$ | Military, government, secure phone for tough jobs |
Security chip, encrypted calls, luxury build | Android | $$$ | Executives, VIPs, luxury | |
Samsung Galaxy A36 5G | Samsung Knox, secure folder, biometrics | Android | $ | Budget, students, secure phone for value |
Google Pixel 9a | Security chip, long-term updates, encryption | Android | $ | Families, long-term use |
OnePlus Nord 4 | Secure boot, privacy mode, biometrics | Android | $ | Young pros, students |
Apple iPhone 16 Pro Max | Secure Enclave, Face/Touch ID, iOS updates | iOS | $$ | iOS fans, business |
Tip: If you need a secure phone for work, pick one with strong encryption and updates. For privacy, hardware kill switches and open-source systems help you keep your data safe.
This table helps you match your needs to the right secure phone. Some secure phones are best for work. Others are good for privacy or saving money. You get to choose what is most important. If you want a phone that lasts, look at how long it gets updates. If you need a phone for tough jobs, pick one with tamper-proof hardware.
All the secure phones in this list give strong protection. You just need to choose the secure phone that fits your life.
Tips for Secure 5G Phones
Everyday Security Practices
You use your secure phone for many things. Keeping it safe is not hard. Try these easy steps to protect your secure 5g phones each day:
Always update your phone when you see a new update. Updates fix problems that hackers want to use.
Only get apps from trusted stores. Some apps can steal your private data.
Use strong passwords. Do not use the same password for more than one account.
Turn on fingerprint or face unlock. This makes your secure phone harder to get into.
Check what apps can do. If an app wants your location or camera and you do not know why, say no.
Stay away from public Wi-Fi. If you must use it, turn on a VPN to keep your secure communication safe.
Turn off Bluetooth when you are not using it. Hackers can use Bluetooth to get into your secure 5g phones.
Back up your data often. If you lose your secure phone, you will not lose your photos or private data.
Tip: Set your secure phone to get regular security patches. This keeps your device safe from new threats.
Advanced Tips for Business
If you use secure 5g phones for work, you have private data every day. You need extra steps to keep your business safe:
Mistake | What Can Happen |
|---|---|
Leaves your secure phone open to attack | |
Weak passwords | Makes it easy for hackers to get in |
No employee training | Staff may fall for phishing or scams |
No device management | Lost phones can leak sensitive data |
Here are some ways to make your security better:
Use multi-factor authentication on every secure phone.
Set up Mobile Device Management. This lets you lock or erase a lost device.
Teach your team how to spot fake messages and phishing.
Give workers secure 5g phones with encrypted data transfers.
Make a clear rule for handling private data.
Give safe options instead of public Wi-Fi, like company hotspots.
Note: Secure 5g phones with regular security patches and updates help you stay safe from threats. Protect your private data and keep your business working well.
Choosing the right secure phone matters for your safety. You want a secure phone that fits your life and keeps your data safe. Take time to learn about each secure phone and its features. When you use a secure phone, you protect your privacy every day. Try the tips above to get the most from your secure phone. Stay alert and update your secure phone often. If you use a secure phone for work, talk to an expert. A secure phone gives you peace of mind.
Remember, a secure phone is your best tool for staying safe in today’s world.
FAQ
What makes a secure phone different from a regular smartphone?
A secure phone has more ways to keep you safe. It uses things like hardware encryption and secure boot. You also get privacy controls. Regular phones might not have these tools. With a secure phone, hackers have a harder time getting your data.
How often should you update your secure phone?
Update your secure phone right when you see an update. Updates fix problems that hackers could use. If you wait, your phone could be easier to attack.
Can you use a secure phone for both work and personal life?
Yes, you can use one secure phone for both. Many secure phones help you keep work and personal stuff apart. This means you get privacy and security for everything.
Do you need special apps for a secure phone?
Most secure phones let you use normal apps. Some have private app stores or safer apps. You can use your favorite apps, but always check if they keep your data safe.
Is a secure phone worth the price?
Secure phones cost more, but they help protect your privacy. You keep your data and work safe. If you want to stay safe, a secure phone is a good choice.






