You want to keep your personal data safe. In 2025, experts say Secure Mobile Phones like the Purism Librem 5 are the best. This phone is special because it has hardware kill switches. It also uses open-source software. Today, keeping your smartphone safe is very important. Hackers and data trackers try to get into your device every day. Picking a phone with good privacy features helps protect you.
Key Takeaways
-
Pick a secure phone to keep your data safe from hackers and trackers.
-
Find phones with strong encryption, regular updates, and privacy controls.
-
Think about phones that have hardware kill switches and open-source software for better privacy.
-
Always look at app permissions and be careful with public Wi-Fi to keep your phone safe.
-
Good habits, like using strong passwords and backing up your data, help protect your privacy.
Top Secure Mobile Phones 2025
Picking the right phone helps keep your data safe. Here are the most secure smartphones you can buy in 2025. Each phone has strong privacy tools, good encryption, and gets updates often. These are the best secure smartphones for people who want to keep their info private.
Blackphone PRIVY 2.0
Some people want a phone that cares about privacy. The Blackphone PRIVY 2.0 is made for that. It uses a special operating system for security. You can make encrypted calls, texts, and emails. The phone blocks trackers and lets you control app permissions. It gets updates to fix new problems. If you want a top encrypted phone, this is a good choice.
Google Pixel with Graphene OS
If you like Android but want more privacy, try the Google Pixel with Graphene OS. This phone uses a special Android version with more protection. You get things like better app sandboxing, scoped permissions, and a safer web browser. You can set a duress PIN to wipe your data if needed. Here’s what makes it special:
|
Feature |
الوصف |
|---|---|
|
Apps run in a safe space and can’t get your private info. |
|
|
Scoped Permissions |
You choose what files or contacts an app can see. |
|
Duress PINs |
Use a secret code to erase your data in an emergency. |
|
Hardened Web Browser |
Keeps your browsing private and safe. |
|
Auto Reboot |
The phone restarts itself to stop hackers from stealing data. |
|
Multi-User Profiles |
You can make different profiles to keep apps and data apart. |
|
Extra Permissions |
Stops apps from seeing your device ID or what you do. |
This phone is great for people who want control and to feel safe.
Bittium Tough Mobile 2C
Some people need a phone with government-level security. The Bittium Tough Mobile 2C is built for that. It passes hard security tests and has certifications like Common Criteria and FIPS 140-2. The phone uses strong encryption and has anti-tampering tools. It also stops eavesdropping. Many groups trust this phone with important data. If you want a very secure smartphone, this is a top pick.
|
Security Feature |
Details |
|---|---|
|
Certifications |
|
|
Encryption |
Strong, with anti-tampering and anti-eavesdropping |
|
Trusted by |
Governments and companies |
Purism Librem 5
Some people want a phone that is open and easy to check for problems. The Purism Librem 5 uses PureOS, a Linux system anyone can look at or fix. The phone keeps the modem and CPU apart, which lowers hacking risks. You can use hardware kill switches to turn off the camera, mic, WiFi, or Bluetooth. The Librem 5 has a smartcard reader for safe logins and storing keys. This makes it a top encrypted phone for privacy fans.
-
Runs PureOS, an open-source system
-
Modem and CPU are kept apart
-
Hardware kill switches for wireless, camera, and mic
-
Smartcard reader for safe logins
K-iPhone
If you want an iPhone with more privacy, check out the K-iPhone. It uses Apple’s security and adds more privacy tools. You get encrypted calls and texts, plus apps that block trackers. The phone lets you control what data apps can use. Updates keep your phone safe from new threats. This phone is great for people who want both privacy and easy use.
Sirin Labs Finney U1
Are you interested in blockchain? The Sirin Labs Finney U1 uses blockchain to keep your transactions and data safe. Every transaction is secure, clear, and can’t be changed. The phone uses decentralized authentication and strong encryption to protect your digital identity. If you want a good encrypted phone for digital assets, this is a smart choice.
Tip: If you use cryptocurrencies or care about digital wallets, the Finney U1 gives you extra peace of mind.
Apple iPhone 17 Pro
Apple keeps making secure mobile phones better. The iPhone 17 Pro has new privacy features, like eSIM technology. You don’t need a physical SIM card that someone could steal. If you lose your phone, the eSIM stays locked. The phone also makes it easier to use travel SIMs and has longer battery life. Apple’s updates and privacy tools make this one of the safest smartphones.
|
Feature |
iPhone 17 Pro Enhancements |
|---|---|
|
eSIM Technology |
More secure, no physical SIM to steal |
|
Security |
eSIM stays locked if phone is lost or stolen |
|
International Roaming |
Easier travel SIM management |
|
Battery Life |
Extra two hours of video playback |
Samsung Galaxy S25 Ultra
The Samsung Galaxy S25 Ultra is a secure smartphone for 2025. The phone warns you if there is a security problem on your devices. You can check the ‘Security status of your devices’ page to fix things fast. If your phone misses an update, you get a warning. Samsung Knox Enhanced Encrypted Protection (KEEP) gives each app its own private storage. Knox Vault adds hardware that is hard to tamper with. This makes the S25 Ultra a great secure smartphone for people who want strong protection and easy features.
-
Get alerts for security problems on all your Galaxy devices
-
Fix problems quickly from one page
-
App-specific encrypted storage with KEEP
-
Tamper-resistant hardware with Knox Vault
All these secure mobile phones have something special. Some use open-source software, others use hardware or blockchain. They all get updates, use strong encryption, and give you more control over your data. If you want the best encrypted phones or the safest smartphones, these are the top picks for 2025.
Why Secure Mobile Phones Matter
Data Breaches and Threats
You hear about data breaches almost every week. Hackers try to steal your information, like passwords or bank details. Sometimes, they use tricks like phishing or fake apps. If you use your phone for shopping or banking, you face real risks. Even a simple text message can be a trap. When someone gets your data, they can steal your money or pretend to be you. That is why you need a phone that protects you from these threats.
Tip: Always check app permissions before you install anything. If an app asks for too much, it could be risky.
Device-Level Security Importance
Your phone holds your secrets. Photos, messages, and even your location stay on your device. You want to keep all of that safe. Secure phones use special tools to stop hackers. Here’s how some device-level security measures work:
|
Security Measure |
الوصف |
|---|---|
|
You need more than just a password to unlock your phone. |
|
|
Data encryption |
Your data gets scrambled, so only you can read it. |
|
Regular security audits |
The phone checks itself for weak spots and fixes them. |
|
Network access control (NAC) |
Only trusted devices and users can connect to your network. |
Phones with these features make it much harder for anyone to break in. You get peace of mind knowing your private stuff stays private.
Privacy in Daily Life
You use your phone for almost everything—talking to friends, shopping, or paying bills. If your phone is not secure, someone could watch what you do. Privacy matters every day, not just when you hear about a hack. Here are some ways privacy affects your daily life:
-
Encryption keeps your banking and payment info safe from thieves.
-
Your personal messages and photos stay hidden from strangers.
-
Secure phones help you follow privacy laws, like GDPR.
-
You avoid problems like identity theft or fraud.
When you pick a secure phone, you protect your money, your identity, and your peace of mind. You stay in control of your digital life.
Best Secure Smartphones: Features Comparison
Encryption and Privacy Controls
You want your phone to keep secrets safe. The best secure smartphones use strong encryption. This protects your calls, messages, and files. Each phone gives you different privacy controls. Look at this table to compare top phones:
|
الهاتف الذكي |
Encryption Features |
Privacy Controls |
|---|---|---|
|
Blackphone PRIVY 2.0 |
End-to-end encryption for calls and messages |
Blocks Google services, secure boot, remote wipe |
|
Bittium Tough Mobile 2C |
Dual OS, end-to-end encrypted calls and messages |
Tamper-proof design, secure offline mode |
|
Purism Librem 5 |
Full disk encryption, call encryption |
Physical switches for sensors, open-source software |
|
K-iPhone |
End-to-end encryption for voice communications |
No call logs stored, retains iOS experience |
|
Sirin Labs Finney U1 |
Encrypted calls and messaging, three-factor authentication |
Built-in protections for digital assets |
All these phones use strong encryption. Some, like the Purism Librem 5, have switches to turn off the camera or mic. Others, like the Blackphone PRIVY 2.0, block trackers and let you erase data from anywhere. You decide what apps can see and do. This layered security keeps your info safe from hackers and snoops.
Hardware Security and Isolation
Software is not enough to keep you safe. Hardware security adds more protection. The best secure smartphones use special chips and hardware. These keep your data locked away. Here’s a table showing how hardware security works:
|
Device Type |
Key Features |
Security Level |
Use Cases |
|---|---|---|---|
|
Secure Element (SE) |
Tamper-resistant, stores sensitive data |
High |
Mobile phones, smart cards |
|
Trusted Platform Module (TPM) |
Integrated cryptographic keys |
Medium |
PCs, laptops |
|
Hardware Security Module (HSM) |
High cryptographic assurance |
Very High |
Data centers |
|
Trusted Execution Environment (TEE) |
Isolates secure code |
Medium |
Apps needing extra protection |
Phones like the Bittium Tough Mobile 2C use tamper-proof hardware. The Samsung Galaxy S25 Ultra has Knox Vault. Knox Vault keeps your keys and passwords in a safe chip. This layered security means even if someone steals your phone, they cannot get your secrets. You get strong encryption at every level.
Software Updates and Open Source
You want your phone to stay safe for a long time. Frequent updates fix problems and add new security tools. Some brands do this better than others:
-
Google gives seven years of upgrades and security patches for Pixel 8 and newer.
-
Apple supports iPhones for at least six years.
-
Samsung, OnePlus, and OPPO offer good updates, but it depends on the model.
Phones like the Purism Librem 5 use open-source software. Anyone can check the code for problems. This makes strong encryption even better because you know what is inside your phone. Regular updates and open-source systems give you layered security that lasts.
Tip: Always update your phone. You get the newest strong encryption and security fixes.
Pros and Cons of Most Secure Smartphones
Strengths Overview
Secure cell phones have many good points. These phones help you keep your privacy safe. You get more control over your security. The table below shows the main strengths:
|
الهاتف الذكي |
Strengths |
|---|---|
|
Purism Librem 5 |
Full user control, open-source stack, physical privacy controls |
|
Silent Circle Blackphone |
Corporate communication security |
|
Bittium Tough Mobile 2C |
MIL-STD durability, strict separation of data environments |
|
CAT S75 |
IP68/69K protection, emergency communication |
|
Apple iPhone 15 Pro |
Fast updates, deep hardware-software integration, privacy by default |
|
Samsung Galaxy S23 Ultra |
Powerful hardware, enterprise support, real-time threat monitoring |
|
Google Pixel 8 (with GrapheneOS) |
Transparent open-source base, rapid updates, minimal Google tracking |
|
BlackBerry Key3 |
Physical keyboard, enterprise-grade encryption, regular security patches |
You get features like end-to-end encryption and secure boot. Phones have regular updates and biometric locks. Privacy-friendly operating systems help keep your data safe. These strengths protect your phone from threats.
Limitations to Consider
Even the best secure phones have some problems. You should know these before you pick a phone:
-
Use a secure network when you go online. Public Wi-Fi can be risky for your data.
-
Strange links or messages can trick you. Be careful and do not click on things you do not trust.
-
Download apps only from trusted places. Some apps can hide malware or steal your info.
-
Keep your security software updated. Strong passwords help keep your accounts safe.
-
Do not jailbreak your phone. This makes it easier for viruses and hackers to attack.
Secure phones give you strong protection. You still need to help keep your information safe.
Criteria for Choosing the Most Secure Phone
When you want a secure phone, you need to think about more than just the brand. You should check how the phone keeps your data safe. You also need to see if it is easy to use and fits your budget. Let’s look at what is most important when picking a secure phone.
Encryption Standards
You want your phone to have strong encryption. This keeps your messages, photos, and files safe from others. Look for these things in secure android phones and privacy-focused devices:
-
Hardened OS: Pick phones with special operating systems like GrapheneOS or locked-down Android. These help stop hackers.
-
Strong encryption: Make sure your phone uses end-to-end encryption and trusted protocols like AES-256. This gives your data the best protection.
Hardware and Software Security
A secure phone needs more than just good software. Hardware security protects your device even more. Many attacks try to break the hardware or firmware. If you pick a phone with hardware-based security, you get strong defense against these threats. This helps your phone keep working right, even if someone tries to hack it.
Privacy Controls and Updates
You want privacy-focused phones that let you control your info. The most secure phone should have:
-
Secure data encryption for all your information.
-
Two-factor authentication for extra safety.
-
Regular security updates to fix problems fast.
-
Strong user authentication.
-
Frequent app testing to find hidden risks.
-
Easy privacy settings and app permissions.
-
Secure code development.
-
App store security checks.
-
Tips and alerts to help you stay safe.
Phones that update often and let you manage your privacy give you the best security.
Budget and Usability
Not everyone can buy the most expensive secure android phones. Cheaper models may not have every advanced feature, but you can still find a secure phone that fits your needs. Some affordable brands, like OnePlus and Samsung, offer good encryption and less extra software. You get good privacy without spending too much.
Tip: Always balance your need for security with how easy the phone is to use. The best secure phone is the one you feel comfortable using every day.
Tips to Maximize Mobile Security

Best Practices
You want your phone to be safe every day. Always update your operating system and apps. Updates fix bugs and stop hackers. Set a strong password or use your fingerprint to unlock. Turn on encryption to keep your files safe. Use a VPN when you use public Wi-Fi. This keeps your data private from others. Turn on remote wipe and lock features. If you lose your phone, you can erase your data. Back up your data often. If your phone breaks, you will not lose your stuff. Check your device activity for anything strange. If you see something odd, act quickly.
Tip: Use secure messaging apps for private chats. These apps keep your conversations safe from others.
Recommended Security Apps
You can make your phone safer with the right apps. Privacy Dashboard shows which apps use your camera, mic, or location. Bouncer lets you give apps permission for a short time. Use 1Password or Bitwarden to keep your passwords safe. ProtonMail keeps your emails private. Signal Private Messenger is great for secure messages and calls. Solid Explorer File Manager adds encryption to your files. Pay by Privacy.com makes virtual cards for safe shopping. NordVPN or ExpressVPN protects your data on public Wi-Fi.
-
Privacy Dashboard: Shows app permissions in real time.
-
Bouncer: Lets you control app access to your data.
-
1Password / Bitwarden: Stores passwords with strong encryption.
-
ProtonMail: Sends encrypted emails.
-
Signal Private Messenger: Sends secure texts and calls.
-
Solid Explorer File Manager: Encrypts files and folders.
-
Pay by Privacy.com: Lets you shop online with virtual cards.
-
NordVPN / ExpressVPN: Encrypts your internet traffic.
Note: Secure messaging apps like Signal keep your chats private, even if someone tries to spy on you.
Avoiding Common Risks
You face many risks when you use your phone. Some are easy to avoid if you know what to do. Here is a table that shows common risks and how to stay safe:
|
Risk Type |
How to Avoid It |
|---|---|
|
Insecure Data Storage |
Encrypt important data. Use smart storage. Check storage rules. |
|
Weak Authentication Mechanisms |
Use multi-factor authentication. Make strong, unique passwords. Store passwords safely. |
|
Insufficient Cryptography |
Use trusted encryption. Update cryptography tools. Encrypt data end-to-end. |
|
Improper Session Handling |
Always use HTTPS with TLS. Check server certificates. Review network security. |
|
Poor Code Quality |
Follow safe coding rules. Check system security. Check and clean inputs. |
|
Lack of Regular Security Updates |
Install patches often. Check security. Learn about updates. |
|
Insecure API Connections |
Use HTTPS and TLS for APIs. Use strong authentication. Check APIs. |
|
Unprotected User Data |
Encrypt data at rest and in transit. Use strict access controls. Check security. |
Always use secure messaging for private talks. Never share passwords or private info in normal texts. Pick apps with secure messaging and strong encryption. If you use secure messaging, you lower your risk of leaks and hacks. Stay alert and do not click on strange links. Protect your phone to protect your life.
You can pick from many secure mobile phones. Some phones, like the Google Pixel with Graphene OS, have strong privacy features. Others, like the Purism Librem 5, let you control your privacy. Some brands, like Samsung, have had problems with privacy and data collection. Look at the table to see what is important when choosing a phone:
|
Feature |
الوصف |
|---|---|
|
App and Data Permissions |
You choose what apps can see |
|
Regular Security Updates |
Updates fix new security problems |
|
Privacy-Focused Browsing |
Stops trackers and limits data collection |
|
Data Encryption |
Strong encryption keeps your data safe |
|
Secure Operating Systems |
Open-source software helps you see what is inside |
|
User Behavior |
Good habits keep your phone safe |
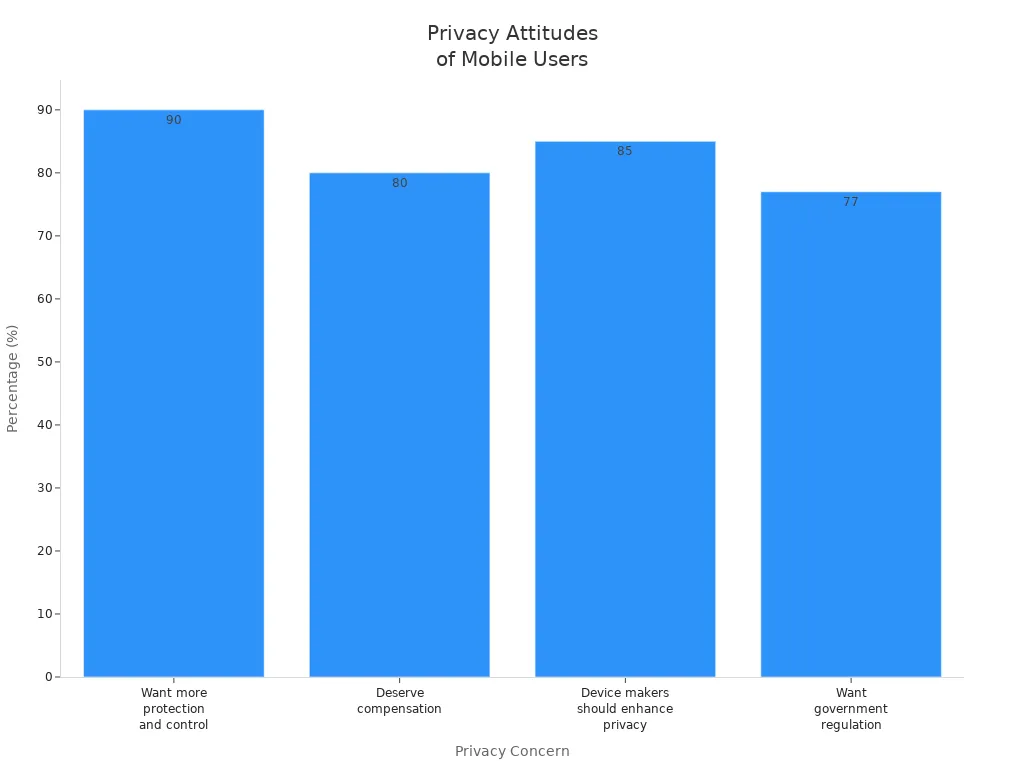
Most people want to keep their data safe and private. You can make your phone more private by doing easy things:
-
Lock your phone and use strong passwords.
-
Update your software often.
-
Be careful with public Wi-Fi and apps you download.
-
Back up your data so you do not lose it.
You do not need a pricey phone to stay private. Good habits and smart choices help a lot. Start protecting your privacy now.
التعليمات
What makes a phone truly secure for privacy-conscious users?
You need a phone with strong security tools. Look for military-grade encryption and privacy controls. End-to-end encryption is important too. Phones with encrypted communications help keep your data safe. Cutting-edge encryption technology is also helpful. Regular updates make your phone safer and more private.
Can I use secure communication apps on any smartphone?
Most phones let you install secure communication apps. These apps use encrypted communications to protect your messages. Privacy controls help keep your chats safe. For better security, pick phones with built-in data encryption. End-to-end encryption is a good feature to have. Some phones give you extra privacy controls to stop cyber threats.
How do privacy controls help protect my personal information?
Privacy controls let you choose what apps can see. You can block tracking and change permissions. This keeps your data private. Phones with advanced privacy controls help you stay safe. Encrypted communications give you more control over your security.
Is there such a thing as an unhackable smartphone?
No phone is totally unhackable. You can get close with military-grade encryption and strong privacy controls. Encrypted communications help too. Regular updates and new encryption technology keep you safer. These features help you stay ahead of threats.
Why should I care about end-to-end encryption and data encryption?
End-to-end encryption keeps your messages private all the way. Data encryption protects files on your phone. Both make your phone more secure and private. You want these features to keep your info safe. They help protect you from cyber threats.








